SY0-601 Exam Question 11
Which of the following describes the exploitation of an interactive process to gain access to restncted areas?
SY0-601 Exam Question 12
A technician enables full disk encryption on a laptop that will be taken on a business tnp. Which of the following does this process BEST protect?
SY0-601 Exam Question 13
Which of the following employee roles is responsible for protecting an organization's collected personal information?
SY0-601 Exam Question 14
Several users have opened tickets with the help desk. The help desk has reassigned the tickets to a secunty analyst for further review The security analyst reviews the following metrics:
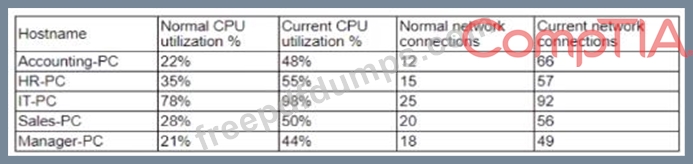
Which of the following is MOST likely the result of the security analyst's review?

Which of the following is MOST likely the result of the security analyst's review?
SY0-601 Exam Question 15
A security analyst in a SOC has been tasked with onboarding a new network into the SIEM. Which of the following BEST describes the information that should feed into a SIEM solution in order to adequately support an investigation?

