SY0-601 Exam Question 416
A company discovered that terabytes of data have been exfiltrated over the past year after an employee clicked on an email link. The threat continued to evolve and remain undetected until a security analyst noticed an abnormal amount of external connections when the employee was not working. Which of the following is the MOST likely threat actor?
SY0-601 Exam Question 417
A security analyst is investigating some users who are being redirected to a fake website that resembles www.comptia.org. The following output was found on the naming server of the organization:
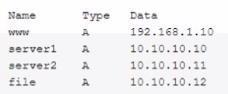
Which of the following attacks has taken place?

Which of the following attacks has taken place?
SY0-601 Exam Question 418
A customer called a company's security team to report that all invoices the customer has received over the last five days from the company appear to have fraudulent banking details. An investigation into the matter reveals the following
* The manager of the accounts payable department is using the same password across multiple external websites and the corporate account.
* One of the websites the manager used recently experienced a data breach
* The manager's corporate email account was successfully accessed in the last fve days by an IP address located in a foreign country Which of the following attacks has MOST hkely been used to compromise the manager's corporate account?
* The manager of the accounts payable department is using the same password across multiple external websites and the corporate account.
* One of the websites the manager used recently experienced a data breach
* The manager's corporate email account was successfully accessed in the last fve days by an IP address located in a foreign country Which of the following attacks has MOST hkely been used to compromise the manager's corporate account?
SY0-601 Exam Question 419
The Chief Information Security Officer (CISO) has requested that a third-party vendor provide supporting documents that show proper controls are in place to protect customer data. Which of the following would be BEST for the third-party vendor to provide to the CISO?
SY0-601 Exam Question 420
Which of the following BEST describes the method a security analyst would use to confirm a file that is downloaded from a trusted security website is not altered in transit or corrupted using a verified checksum?

