SY0-601 Exam Question 231
When selecting a technical solution for identity management, an architect chooses to go from an in-house to a third-party SaaS provider. Which of the following risk management strategies is this an example of?
SY0-601 Exam Question 232
Given the following logs:
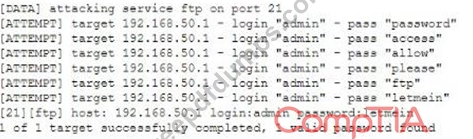
Which of the following BEST describes the type of attack that is occurring?

Which of the following BEST describes the type of attack that is occurring?
SY0-601 Exam Question 233
A security analyst must determine if either SSH or Telnet is being used to log in to servers. Which of the following should the analyst use?
SY0-601 Exam Question 234
A security assessment found that several embedded systems are running unsecure protocols. These Systems were purchased two years ago and the company that developed them is no longer in business Which of the following constraints BEST describes the reason the findings cannot be remediated?
SY0-601 Exam Question 235
Aconbgany uses a drone for precise perimeter and boundary monitoring. Which of the following should be MOST conceming to the company?

