SY0-601 Exam Question 246
A security analyst is reviewing web-application logs and finds the following log:
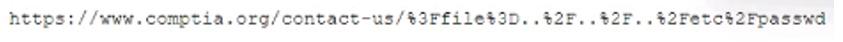
Which of the following attacks is being observed?
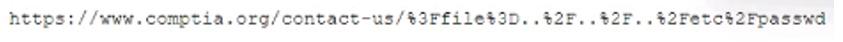
Which of the following attacks is being observed?
SY0-601 Exam Question 247
Which of the following is an example of transference of risk?
SY0-601 Exam Question 248
A security analyst Is investigating a malware incident at a company. The malware is accessing a command-and-control website at www.comptia.com. All outbound Intemet traffic is logged to a syslog server and stored in / logfiles/messages. Which of the following commands would be BEST for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?
SY0-601 Exam Question 249
A Chief Security Officer (CSO) is concerned about the volume and integrity of sensitive information that is exchanged between the organization and a third party through email. The CSO is particularly concerned about an unauthorized party who is intercepting information that is in transit between the two organizations. Which of the following would address the CSO's concerns?
SY0-601 Exam Question 250
Which of the following provides a calculated value for known vulnerabilities so organizations can prioritize mitigation steps?

