SY0-601 Exam Question 1
A security researcher has alerted an organization that its sensitive user data was found for sale on a website. Which of the following should the organization use to inform the affected parties?
SY0-601 Exam Question 2
During an investigation, events from two affected servers in the same subnetwork occurred at the same time:
Server 1: 192.168.10.1 [01/Apr/2021:06:00:00 PST] SAN access denied for user 'admin' Server 2:
192.168.10.6 [01/Apr/2021:06:01:01 CST] SAN access successful for user 'admin Which of the following should be consistently configured to prevent the issue seen in the logs?
Server 1: 192.168.10.1 [01/Apr/2021:06:00:00 PST] SAN access denied for user 'admin' Server 2:
192.168.10.6 [01/Apr/2021:06:01:01 CST] SAN access successful for user 'admin Which of the following should be consistently configured to prevent the issue seen in the logs?
SY0-601 Exam Question 3
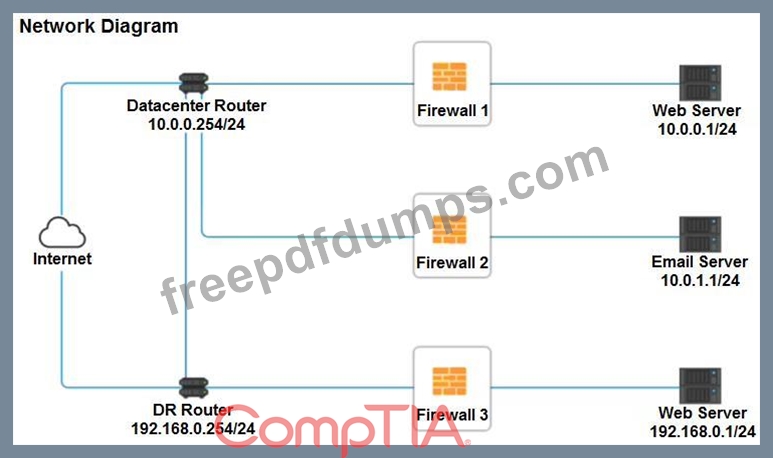
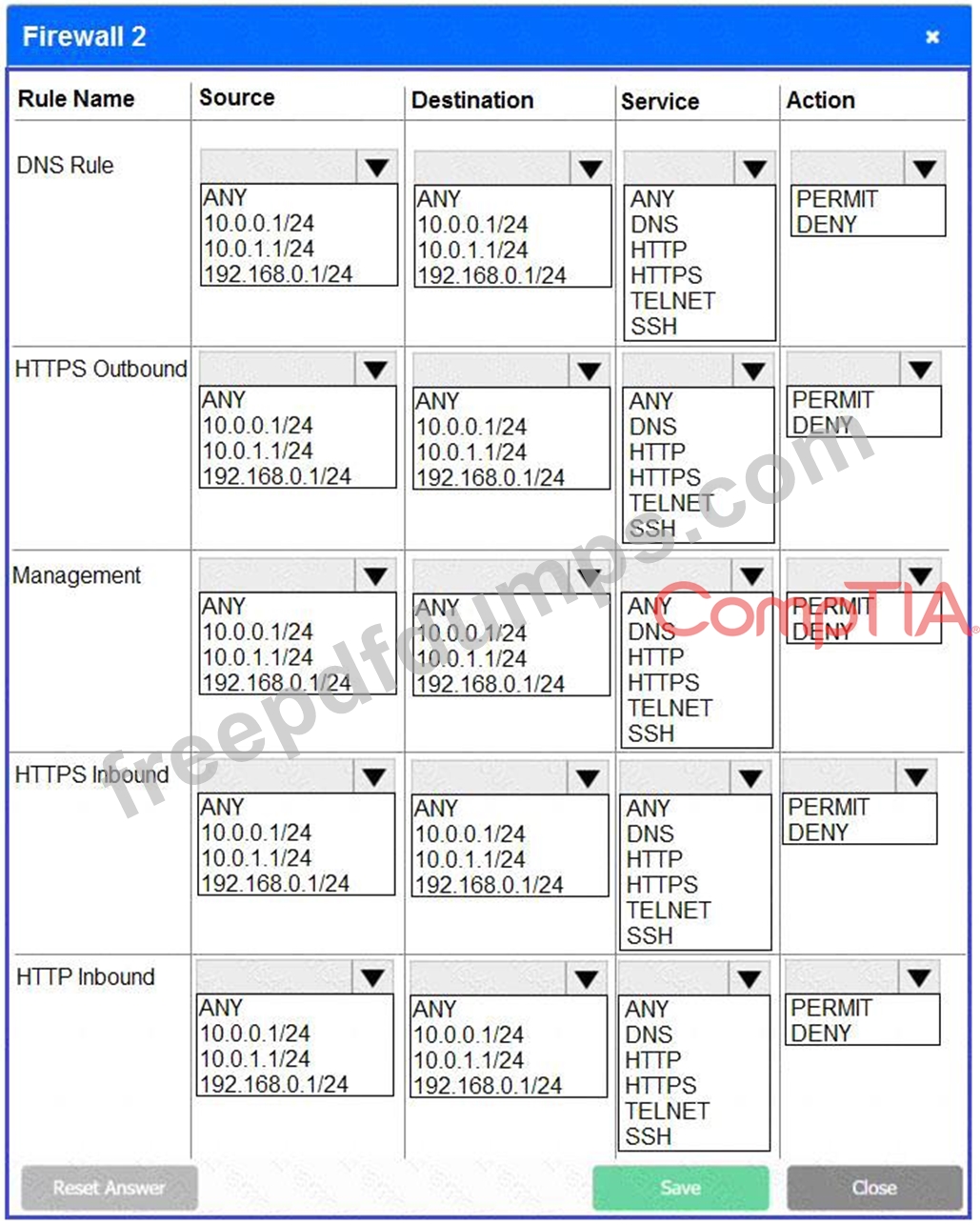
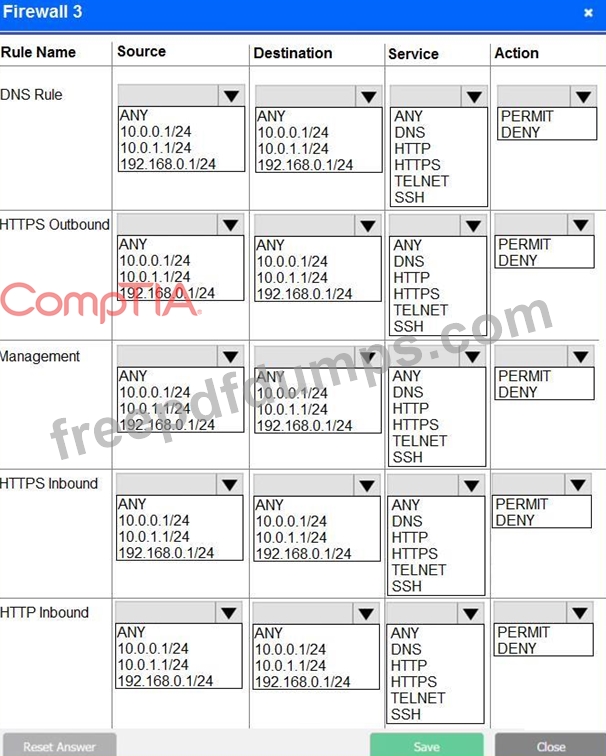
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
* Deny cleartext web traffic.
* Ensure secure management protocols are used. Please Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
INSTRUCTIONS
Click on each firewall to do the following:
* Deny cleartext web traffic.
* Ensure secure management protocols are used. Please Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.



SY0-601 Exam Question 4
A security analyst is concerned about critical vulnerabilities that have been detected on some applications running inside containers. Which of the following is the BEST remediation strategy?
SY0-601 Exam Question 5
The management team has requested that the security team implement 802.1X into the existing wireless network setup. The following requirements must be met:
* Minimal interruption to the end user
* Mutual certificate validation
Which of the following authentication protocols would meet these requirements?
* Minimal interruption to the end user
* Mutual certificate validation
Which of the following authentication protocols would meet these requirements?



