SYO-501 Exam Question 71
Which of the following describes the ability of code to target a hypervisor from inside a guest OS?
SYO-501 Exam Question 72
An attachment that was emailed to finance employees contained an embedded message. The security administrator investigates and finds the intent was to conceal the embedded information from public view. Which of the following BEST describes this type of message?
SYO-501 Exam Question 73
A penetration testing is preparing for a client engagement in which the tester must provide data that proves and validates the scanning tools' results.
Which of the following is the best method for collecting this information?
Which of the following is the best method for collecting this information?
SYO-501 Exam Question 74
Ann, a user, reports she is unable to access an application from her desktop. A security analyst verifies Ann's access and checks the SIEM for any errors. The security analyst reviews the log file from Ann's system and notices the following output:

Which of the following is MOST likely preventing Ann from accessing the application from the desktop?

Which of the following is MOST likely preventing Ann from accessing the application from the desktop?
SYO-501 Exam Question 75
A security administrator suspects that a DDoS attack is affecting the DNS server The administrator accesses a workstation with the hostname of workstation01 on the network and obtains the following output from the if config command:
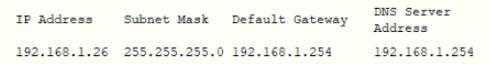
The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occurring?

The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occurring?

