SYO-501 Exam Question 56
A security administrator suspects there may be unnecessary services running on a server. Which of the following tools will the administrator MOST likely use to confirm the suspicions?
SYO-501 Exam Question 57
An Organization requires secure configuration baselines for all platforms and technologies that are used. If any system cannot conform to the secure baseline, the organization must process a risk acceptance and receive approval before the system is placed into production. It may have non-conforming systems in its lower environments (development and staging) without risk acceptance, but must receive risk approval before the system is placed in production. Weekly scan reports identify systems that do not conform to any secure baseline.
The application team receive a report with the following results:
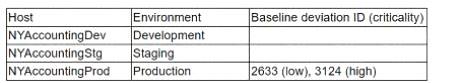
There are currently no risk acceptances for baseline deviations. This is a mission-critical application, and the organization cannot operate If the application is not running. The application fully functions in the development and staging environments. Which of the following actions should the application team take?
The application team receive a report with the following results:

There are currently no risk acceptances for baseline deviations. This is a mission-critical application, and the organization cannot operate If the application is not running. The application fully functions in the development and staging environments. Which of the following actions should the application team take?
SYO-501 Exam Question 58
A security analyst is hardening a server with the directory services role installed. The analyst must ensure LDAP traffic cannot be monitored or sniffed and maintains compatibility with LDAP clients. Which of the following should the analyst implement to meet these requirements? (Select two.)
SYO-501 Exam Question 59
Joe, an employee, wants to show his colleagues how much he knows about smartphones. Joe
demonstrates a free movie application that he installed from a third party on his corporate smartphone.
Joe's colleagues were unable to find the application in the app stores. Which of the following allowed Joe
to install the application? (Select two.)
demonstrates a free movie application that he installed from a third party on his corporate smartphone.
Joe's colleagues were unable to find the application in the app stores. Which of the following allowed Joe
to install the application? (Select two.)
SYO-501 Exam Question 60
An organization wants to conduct secure transactions of large data files. Before encrypting and exchanging the data files, the organization wants to ensure a secure exchange of keys.
Which of the following algorithms is appropriate for securing the key exchange?
Which of the following algorithms is appropriate for securing the key exchange?

