CS0-002 Exam Question 301
A security analyst was alerted to a tile integrity monitoring event based on a change to the vhost- paymonts.conf file.
The output of the diff command against the known-good backup reads as follows
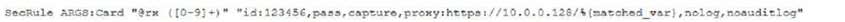
Which of the following MOST likely occurred?
The output of the diff command against the known-good backup reads as follows
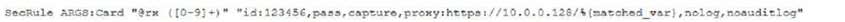
Which of the following MOST likely occurred?
CS0-002 Exam Question 302
An organization supports a large number of remote users. Which of the following is the BEST option to protect the data on the remote users1 laptops?
CS0-002 Exam Question 303
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking
http://<malwaresource>/a.phpin a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the __________.
http://<malwaresource>/a.phpin a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the __________.
CS0-002 Exam Question 304
A retail corporation with widely distributed store locations and IP space must meet PCI requirements relating to vulnerability scanning. The organization plans to outsource this function to a third party to reduce costs.
Which of the following should be used to communicate expectations related to the execution of scans?
Which of the following should be used to communicate expectations related to the execution of scans?
CS0-002 Exam Question 305
Which of the following BEST describes why vulnerabilities found in ICS and SCADA can be difficult to remediate?

