CS0-002 Exam Question 321
The management team assigned the following values to an inadvertent breach of privacy regulations during the original risk assessment:
Probability = 25%
Magnitude = $1,015 per record
Total records = 10,000
Two breaches occurred during the fiscal year. The first compromised 35 records, and the second compromised 65 records. Which of the following is the value of the records that were compromised?
Probability = 25%
Magnitude = $1,015 per record
Total records = 10,000
Two breaches occurred during the fiscal year. The first compromised 35 records, and the second compromised 65 records. Which of the following is the value of the records that were compromised?
CS0-002 Exam Question 322
Given the Nmap request below:
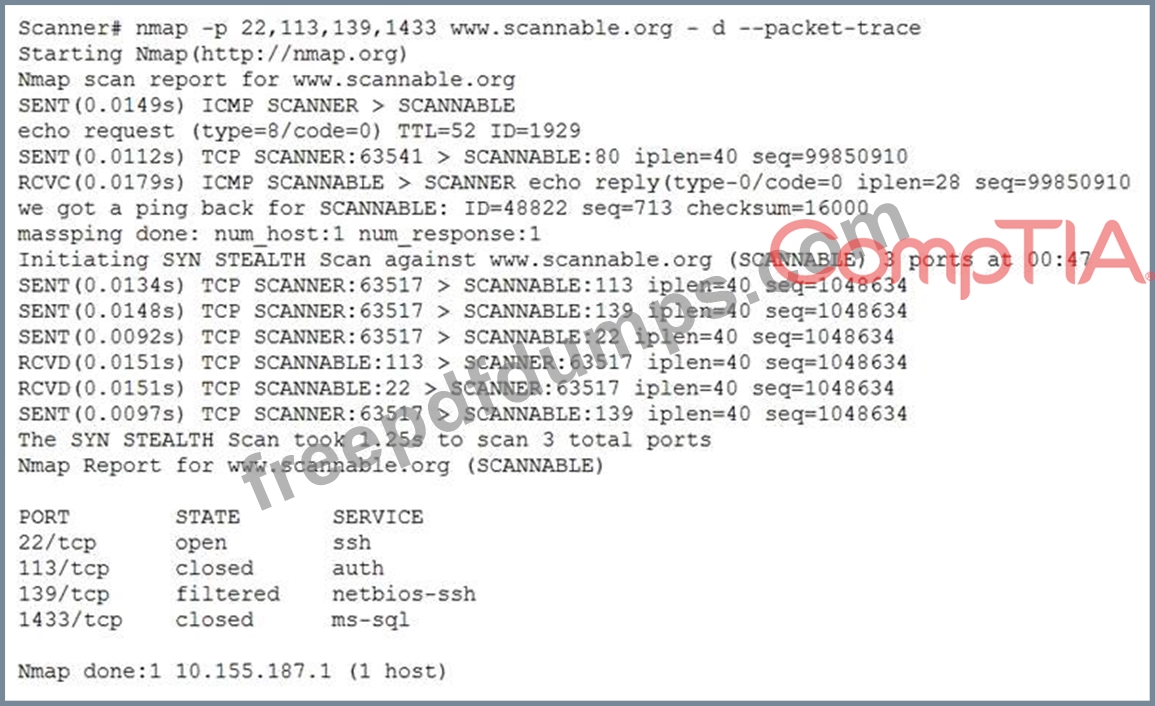
Which of the following actions will an attacker be able to initiate directly against this host?

Which of the following actions will an attacker be able to initiate directly against this host?
CS0-002 Exam Question 323
A security analyst is investigating malicious traffic from an internal system that attempted to download proxy avoidance software as identified from the firewall logs but the destination IP is blocked and not captured. Which of the following should the analyst do?
CS0-002 Exam Question 324
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device. Several of the development phases will occur off-site at the contractor's labs.
Which of the following is the main concern a security analyst should have with this arrangement?
Which of the following is the main concern a security analyst should have with this arrangement?
CS0-002 Exam Question 325
While conducting a network infrastructure review, a security analyst discovers a laptop that is plugged into a core switch and hidden behind a desk.
The analyst sees the following on the laptop's screen:

Which of the following is the BEST action for the security analyst to take?
The analyst sees the following on the laptop's screen:

Which of the following is the BEST action for the security analyst to take?

