CS0-002 Exam Question 86
A security technician is testing a solution that will prevent outside entities from spoofing the company's email domain, which is comptiA.org. The testing is successful, and the security technician is prepared to fully implement the solution.
Which of the following actions should the technician take to accomplish this task?
Which of the following actions should the technician take to accomplish this task?
CS0-002 Exam Question 87
An organization's internal department frequently uses a cloud provider to store large amounts of sensitive dat a. A threat actor has deployed a virtual machine to at the use of the cloud hosted hypervisor, the threat actor has escalated the access rights. Which of the following actions would be BEST to remediate the vulnerability?
CS0-002 Exam Question 88
Which of the following technologies can be used to house the entropy keys for task encryption on desktops and laptops?
CS0-002 Exam Question 89
An analyst is reviewing a list of vulnerabilities, which were reported from a recent vulnerability scan of a Linux server.
Which of the following is MOST likely to be a false positive?
Which of the following is MOST likely to be a false positive?
CS0-002 Exam Question 90
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following:
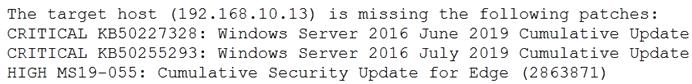
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Tool A reported the following:

Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)

