CS0-002 Exam Question 101
A company wants to establish a threat-hunting team. Which of the following BEST describes the rationale for integration intelligence into hunt operations?
CS0-002 Exam Question 102
Which of the following software assessment methods would be BEST for gathering data related to an application's availability during peak times?
CS0-002 Exam Question 103
A security analyst is reviewing the following DNS logs as part of security-monitoring activities:
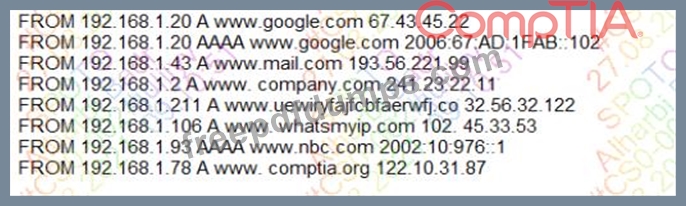
Which of the following MOST likely occurred?

Which of the following MOST likely occurred?
CS0-002 Exam Question 104
While preparing of an audit of information security controls in the environment an analyst outlines a framework control that has the following requirements:
* All sensitive data must be classified
* All sensitive data must be purged on a quarterly basis
* Certificates of disposal must remain on file for at least three years This framework control is MOST likely classified as:
* All sensitive data must be classified
* All sensitive data must be purged on a quarterly basis
* Certificates of disposal must remain on file for at least three years This framework control is MOST likely classified as:
CS0-002 Exam Question 105
A Chief Information Security Officer (CISO) is concerned the development team, which consists of contractors, has too much access to customer dat A.
Developers use personal workstations, giving the company little to no visibility into the development activities.
Which of the following would be BEST to implement to alleviate the CISO's concern?
Developers use personal workstations, giving the company little to no visibility into the development activities.
Which of the following would be BEST to implement to alleviate the CISO's concern?

