312-49v10 Exam Question 51
Gary, a computer technician, is facing allegations of abusing children online by befriending them and sending them illicit adult images from his office computer. What type of investigation does this case require?
312-49v10 Exam Question 52
If a suspect computer is located in an area that may have toxic chemicals, you must:
312-49v10 Exam Question 53
Which of the following techniques can be used to beat steganography?
312-49v10 Exam Question 54
An investigator is searching through the firewall logs of a company and notices ICMP packets that are larger than 65,536 bytes. What type of activity is the investigator seeing?
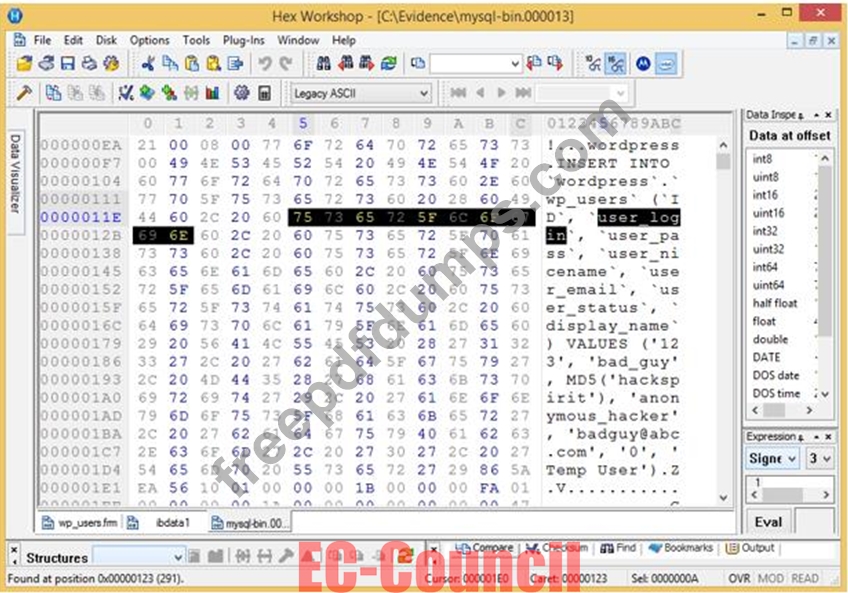
312-49v10 Exam Question 55
Analyze the hex representation of mysql-bin.000013 file in the screenshot below. Which of the following will be an inference from this analysis?