GCCC Exam Question 16
Implementing which of the following will decrease spoofed e-mail messages?
GCCC Exam Question 17
Dragonfly Industries requires firewall rules to go through a change management system before they are configured. Review the change management log. Which of the following lines in your firewall ruleset has expired and should be removed from the configuration?


GCCC Exam Question 18
How can the results of automated network configuration scans be used to improve the security of the network?
GCCC Exam Question 19
An organization has implemented a control for penetration testing and red team exercises conducted on their network. They have compiled metrics showing the success of the penetration testing (Penetration Tests), as well as the number of actual adversary attacks they have sustained (External Attacks). Assess the metrics below and determine the appropriate interpretation with respect to this control.
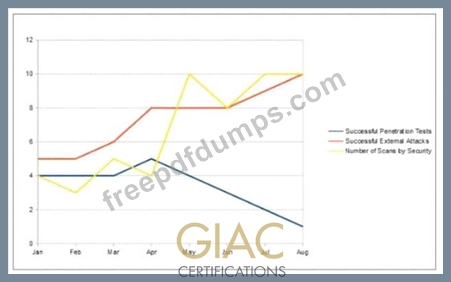

GCCC Exam Question 20
A breach was discovered after several customers reported fraudulent charges on their accounts. The attacker had exported customer logins and cracked passwords that were hashed but not salted. Customers were made to reset their passwords.
Shortly after the systems were cleaned and restored to service, it was discovered that a compromised system administrator's account was being used to give the attacker continued access to the network. Which CIS Control failed in the continued access to the network?
Shortly after the systems were cleaned and restored to service, it was discovered that a compromised system administrator's account was being used to give the attacker continued access to the network. Which CIS Control failed in the continued access to the network?

