GCCC Exam Question 21
If an attacker wanted to dump hashes or run wmic commands on a target machine, which of the following tools would he use?
GCCC Exam Question 22
Which CIS Control includes storing system images on a hardened server, scanning production systems for out-of-date software, and using file integrity assessment tools like tripwire?
GCCC Exam Question 23
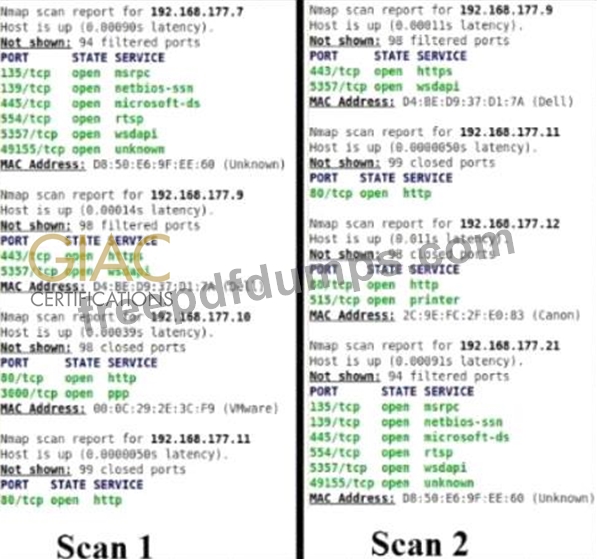
Scan 1 was taken on Monday. Scan 2 was taken of the same network on Wednesday. Which of the following findings is accurate based on the information contained in the scans?

GCCC Exam Question 24
Which of the following will decrease the likelihood of eavesdropping on a wireless network?
GCCC Exam Question 25
An analyst investigated unused organizational accounts. The investigation found that:
-10% of accounts still have their initial login password, indicating they were never used
-10% of accounts have not been used in over six months
Which change in policy would mitigate the security risk associated with both findings?
-10% of accounts still have their initial login password, indicating they were never used
-10% of accounts have not been used in over six months
Which change in policy would mitigate the security risk associated with both findings?

