GCIH Exam Question 201
John, a novice web user, makes a new E-mail account and keeps his password as "apple", his favorite fruit.
John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
GCIH Exam Question 202
Which of the following is used to determine the operating system on the remote computer in a network environment?
GCIH Exam Question 203
Which of the following incident response team members ensures that the policies of the organization are enforced
during the incident response?
during the incident response?
GCIH Exam Question 204
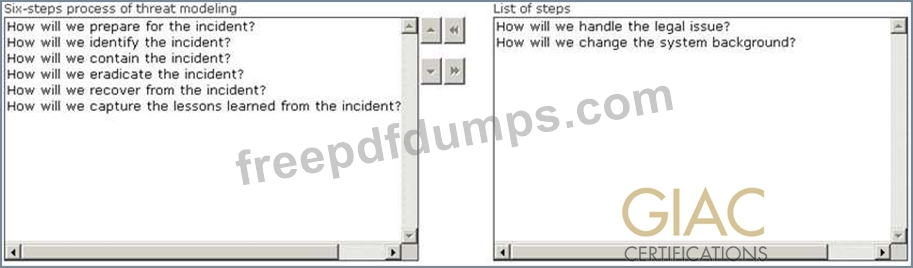
Choose the correct six-step process of threat modeling from the list of different steps.

GCIH Exam Question 205
Who are the primary victims of smurf attacks on the contemporary Internet system?