CISA Exam Question 306
An IS auditor discovers that developers have operator access to the command line of a
production environment operating system. Which of the following controls wou Id BEST mitigate the risk of undetected and unauthorized program changes to the production environment?
production environment operating system. Which of the following controls wou Id BEST mitigate the risk of undetected and unauthorized program changes to the production environment?
CISA Exam Question 307
Sophisticated database systems provide many layers and types of security, including (choose all that apply):
CISA Exam Question 308
The PRIMARY purpose of an IT forensic audit is:
CISA Exam Question 309
When auditing a quality assurance plan, an IS auditor should be MOST concerned if the:
CISA Exam Question 310
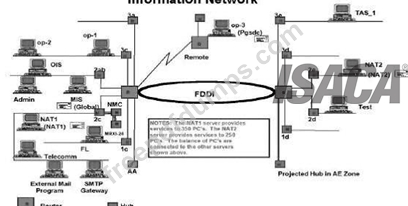
In the 2c area of the diagram, there are three hubs connected to each other. What potential risk might this indicate?