AZ-801 Exam Question 46
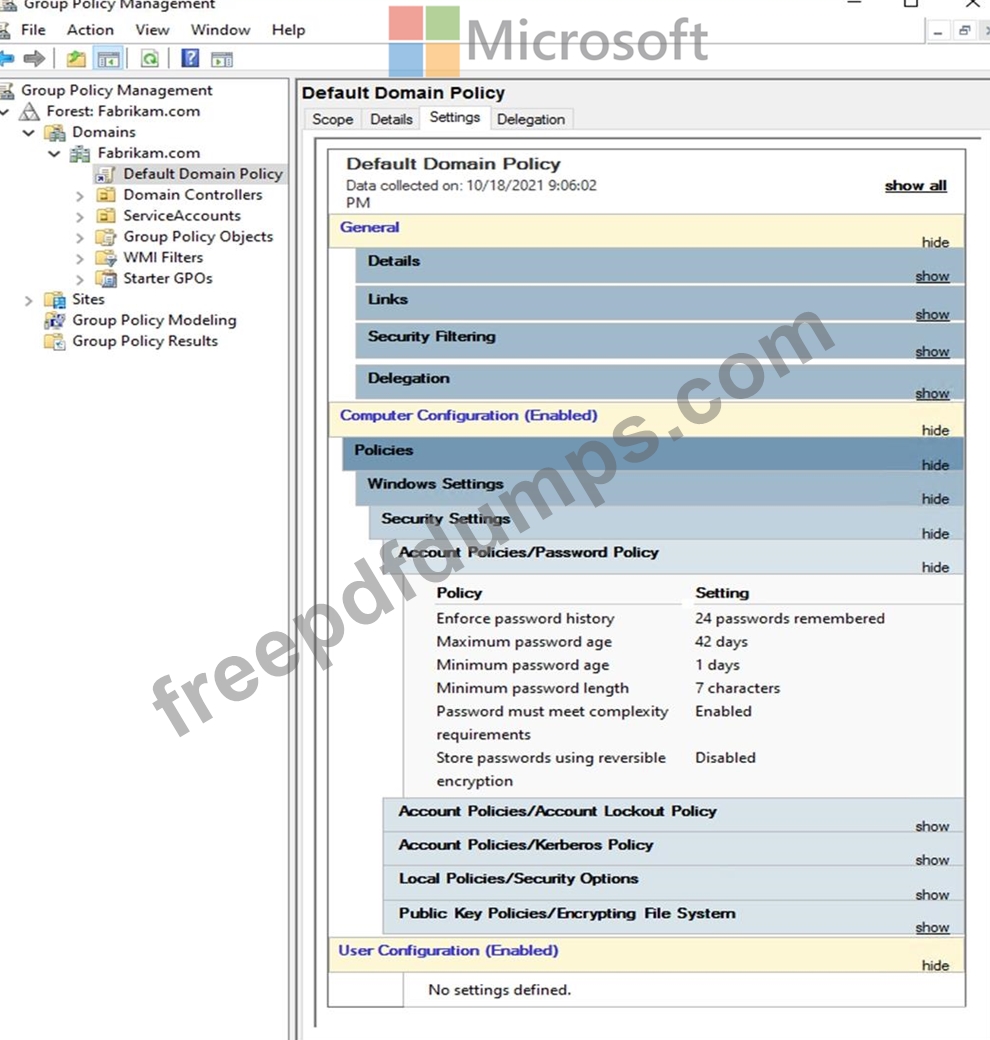
The Default Domain Policy Group Policy Object (GPO) is shown in the GPO exhibit. (Click the GPO tab.)
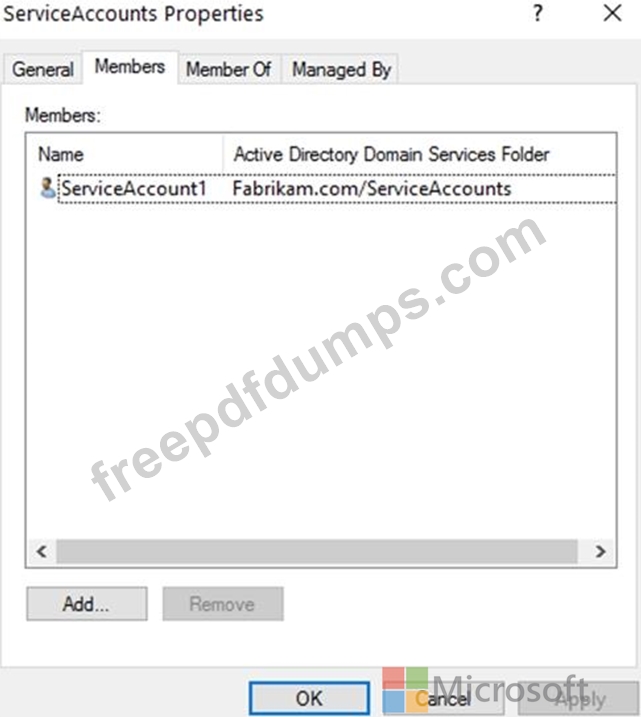
The members of a group named Service Accounts are shown in the Group exhibit. (Click the Group tab.)
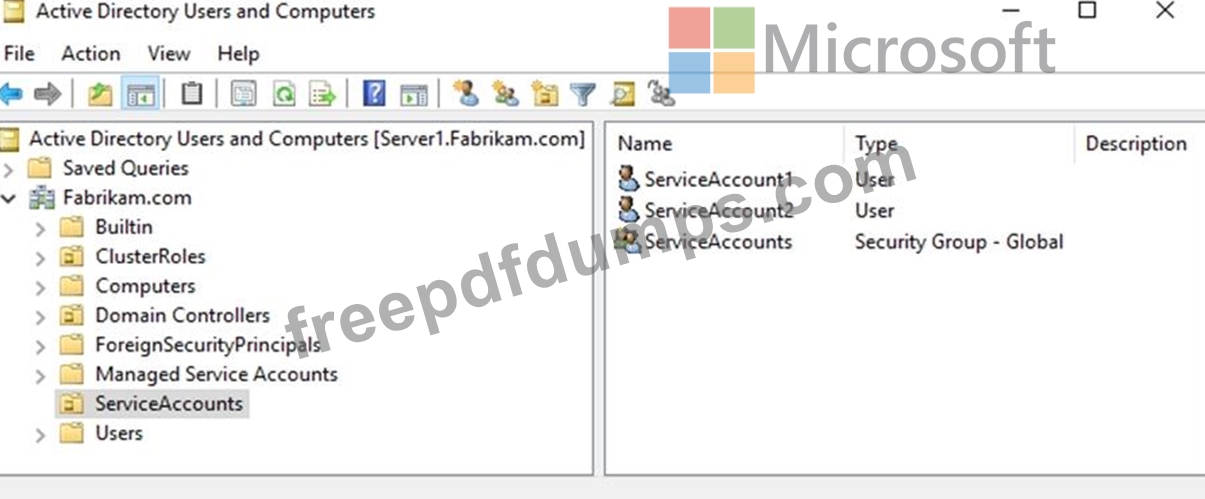
An organizational unit (OU) named ServiceAccounts is shown in the OU exhibit. (Click the OU tab.)
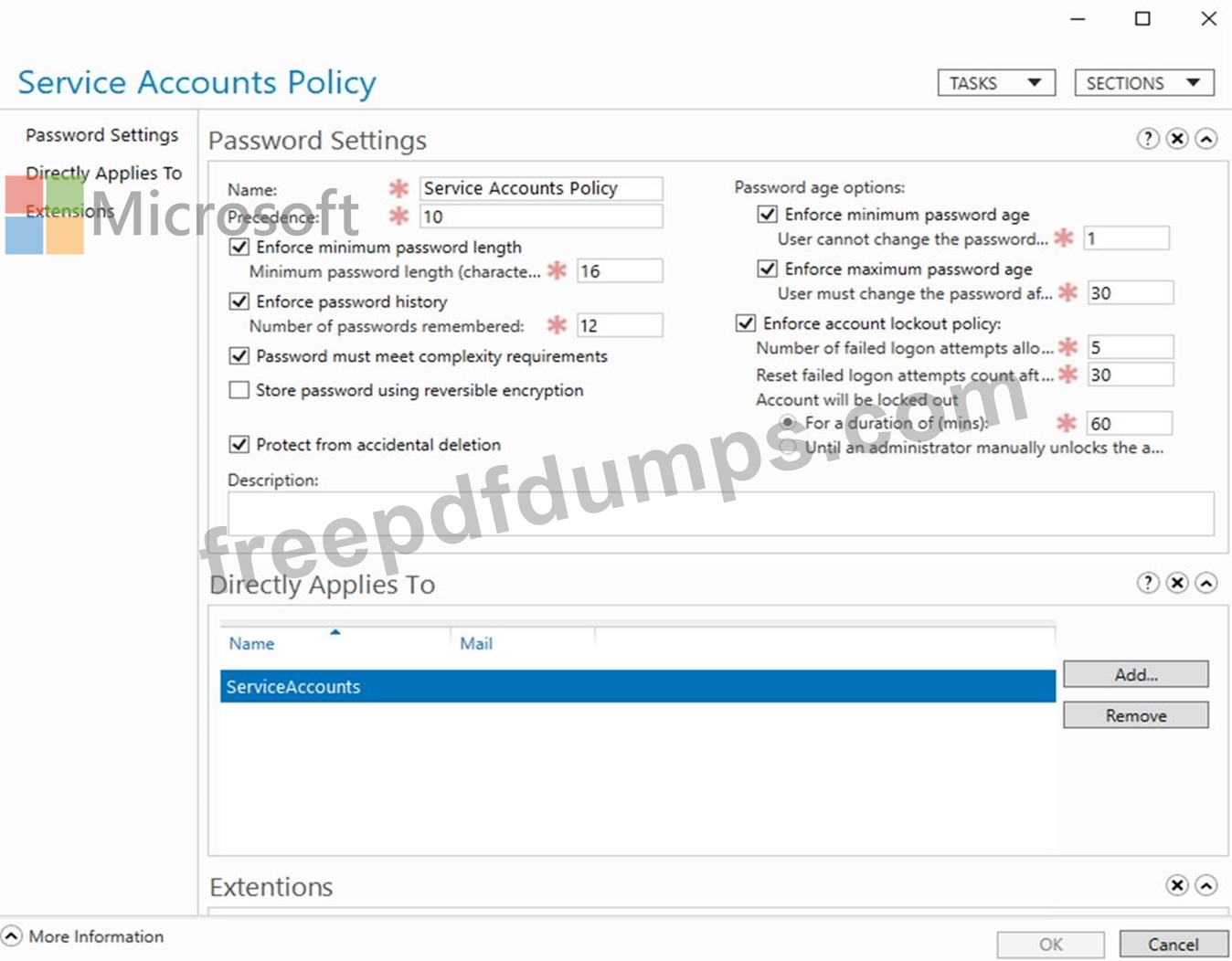
You create a Password Settings Object (PSO) as shown in the PSO exhibit. (Click the PSO tab.)
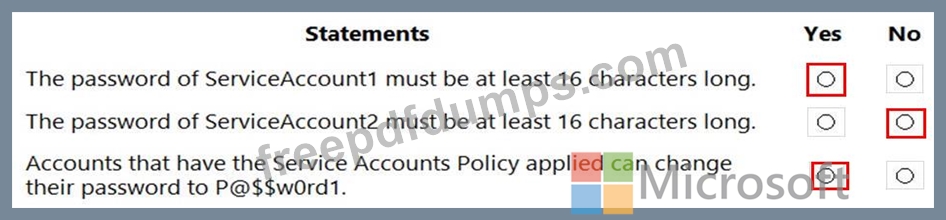
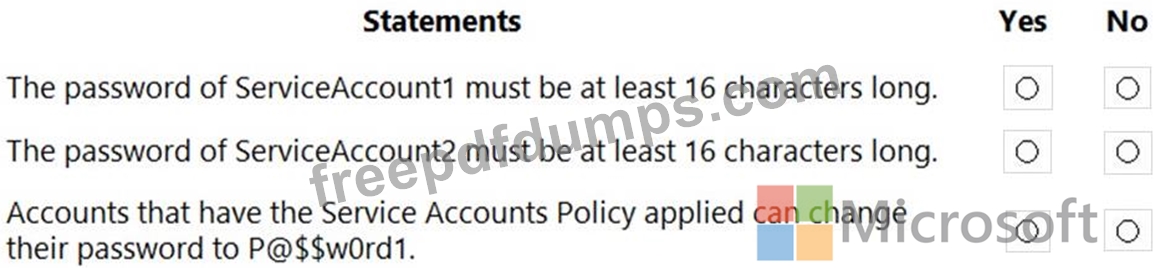
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

The members of a group named Service Accounts are shown in the Group exhibit. (Click the Group tab.)

An organizational unit (OU) named ServiceAccounts is shown in the OU exhibit. (Click the OU tab.)

You create a Password Settings Object (PSO) as shown in the PSO exhibit. (Click the PSO tab.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-801 Exam Question 47
You have a server named Server1 that runs Windows Server and has the Web Server (IIS) server role installed. Server1 hosts an ASP.NET Core web app named WebApp1 and the app's source files.
You install Docker on Server1.
You need to ensure that you can deploy WebApp1 to an Azure App Service web app from the Azure Container Registry.
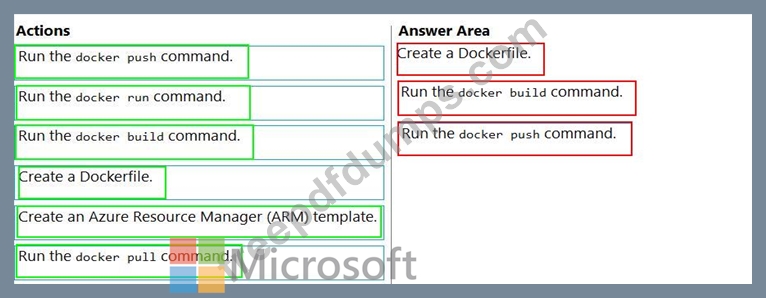
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You install Docker on Server1.
You need to ensure that you can deploy WebApp1 to an Azure App Service web app from the Azure Container Registry.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

AZ-801 Exam Question 48
You have a server that runs Windows Server and has the Web Server (IIS) server role installed. Server1 hosts a single website that has the following configurations:
Is accessible by using a URL of https://www.contoso.com:8443 and has an SSL certificate that was issued by a third-party certification authority (CA) in the Microsoft Trusted Root Program Uses anonymous authentication Was developed by using PHP You plan to use APP Service Migration Assistant to migrate the website to Azure App Service.
You need to migrate the website. The solution must minimize the number of changes made to the existing website.
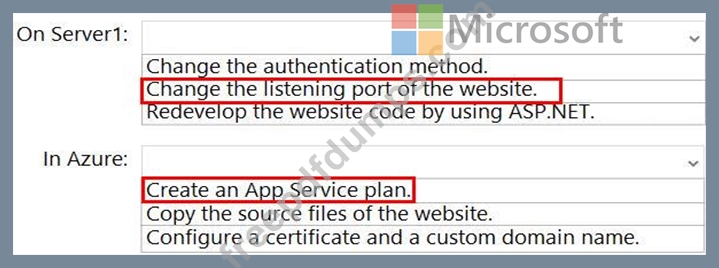
What should you do manually to ensure that the website migration is successful? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
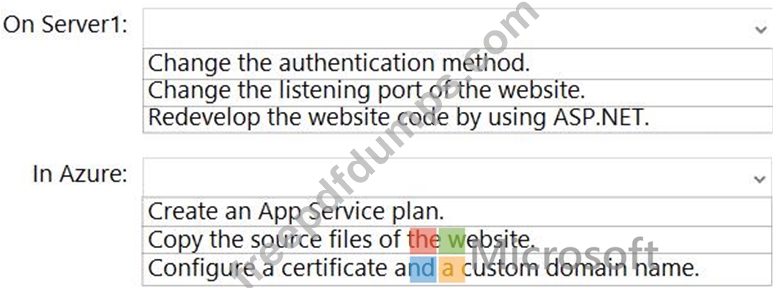
Is accessible by using a URL of https://www.contoso.com:8443 and has an SSL certificate that was issued by a third-party certification authority (CA) in the Microsoft Trusted Root Program Uses anonymous authentication Was developed by using PHP You plan to use APP Service Migration Assistant to migrate the website to Azure App Service.
You need to migrate the website. The solution must minimize the number of changes made to the existing website.
What should you do manually to ensure that the website migration is successful? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-801 Exam Question 49
You have an on-premises server named Served that runs Windows Server. You have an Azure subscription. You plan to back up the files and folders on Server1 to Azure by using Azure Backup. You need to define how long the backups will be retained. What should you use to configure the retention?
AZ-801 Exam Question 50
You have 10 servers that run Windows Server in a workgroup.
You need to configure the servers to encrypt all the network traffic between the servers. The solution must be as secure as possible.
Which authentication method should you configure in a connection security rule?
You need to configure the servers to encrypt all the network traffic between the servers. The solution must be as secure as possible.
Which authentication method should you configure in a connection security rule?