SC-200 Exam Question 56
Your company uses line-of-business apps that contain Microsoft Office VBA macros.
You plan to enable protection against downloading and running additional payloads from the Office VBA macros as additional child processes.
You need to identify which Office VBA macros might be affected.
Which two commands can you run to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.

You plan to enable protection against downloading and running additional payloads from the Office VBA macros as additional child processes.
You need to identify which Office VBA macros might be affected.
Which two commands can you run to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.

SC-200 Exam Question 57
Your on-premises network contains two Active Directory Domain Services (AD DS) domains named contoso.
com and fabrikam.com. Contoso.com contains a group named Group1. Fabrikam.com contains a group named Group2.
You have a Microsoft Sentinel workspace named WS1 that contains a scheduled query rule named Rule1.
Rule1 generates alerts in response to anomalous AD DS security events. Each alert creates an incident.
You need to implement an incident triage solution that meets the following requirements:
Security incidents from contoso.com must be assigned to Group1.
Security incidents from fabrikam.com must be assigned to Group2.
Administrative effort must be minimized.
What should you include in the solution?
com and fabrikam.com. Contoso.com contains a group named Group1. Fabrikam.com contains a group named Group2.
You have a Microsoft Sentinel workspace named WS1 that contains a scheduled query rule named Rule1.
Rule1 generates alerts in response to anomalous AD DS security events. Each alert creates an incident.
You need to implement an incident triage solution that meets the following requirements:
Security incidents from contoso.com must be assigned to Group1.
Security incidents from fabrikam.com must be assigned to Group2.
Administrative effort must be minimized.
What should you include in the solution?
SC-200 Exam Question 58
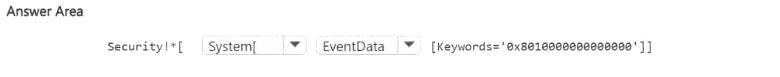
You have an Azure subscription named Sub1. Sub1 contains a Microsoft Sentinel workspace named SW1 and a virtual machine named VM1 that runs Windows Server. SW1 collects security logs from VM1 by using the Windows Security Events via AMA connector.
You need to limit the scope of events collected from VM1. The solution must ensure that only audit failure events are collected.
How should you complete the filter expression for the connector? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to limit the scope of events collected from VM1. The solution must ensure that only audit failure events are collected.
How should you complete the filter expression for the connector? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-200 Exam Question 59
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains 500 Windows devices. As part of an incident investigation, you identify the following suspected malware files:
* sys
* pdf
* docx
* xlsx
You need to create indicator hashes to block users from downloading the files to the devices. Which files can you block by using the indicator hashes?
* sys
* docx
* xlsx
You need to create indicator hashes to block users from downloading the files to the devices. Which files can you block by using the indicator hashes?
SC-200 Exam Question 60
You have a Microsoft Sentinel workspace that has User and Entity Behavior Analytics (UEBA) enabled.
You need to identify all the log entries that relate to security-sensitive user actions performed on a server named Server1. The solution must meet the following requirements:
* Only include security-sensitive actions by users that are NOT members of the IT department.
* Minimize the number of false positives.
How should you complete the query? To answer, select the appropriate options in the answer area. NOTE:
Each correct selection is worth one point.

You need to identify all the log entries that relate to security-sensitive user actions performed on a server named Server1. The solution must meet the following requirements:
* Only include security-sensitive actions by users that are NOT members of the IT department.
* Minimize the number of false positives.
How should you complete the query? To answer, select the appropriate options in the answer area. NOTE:
Each correct selection is worth one point.