SC-200 Exam Question 61
You have an Azure subscription that contains a virtual machine named VM1 and uses Azure Defender. Azure Defender has automatic provisioning enabled.
You need to create a custom alert suppression rule that will supress false positive alerts for suspicious use of PowerShell on VM1.
What should you do first?
You need to create a custom alert suppression rule that will supress false positive alerts for suspicious use of PowerShell on VM1.
What should you do first?
SC-200 Exam Question 62
You have an Azure subscription that contains a user named User1 and a Microsoft Sentinel workspace named WS1.
You need to ensure that User1 can enable User and Entity Behavior Analytics (UEBA) for WS1. The solution must follow the principle of least privilege.
Which roles should you assign to User1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to ensure that User1 can enable User and Entity Behavior Analytics (UEBA) for WS1. The solution must follow the principle of least privilege.
Which roles should you assign to User1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-200 Exam Question 63
Your company has a single office in Istanbul and a Microsoft 365 subscription.
The company plans to use conditional access policies to enforce multi-factor authentication (MFA).
You need to enforce MFA for all users who work remotely.
What should you include in the solution?
The company plans to use conditional access policies to enforce multi-factor authentication (MFA).
You need to enforce MFA for all users who work remotely.
What should you include in the solution?
SC-200 Exam Question 64
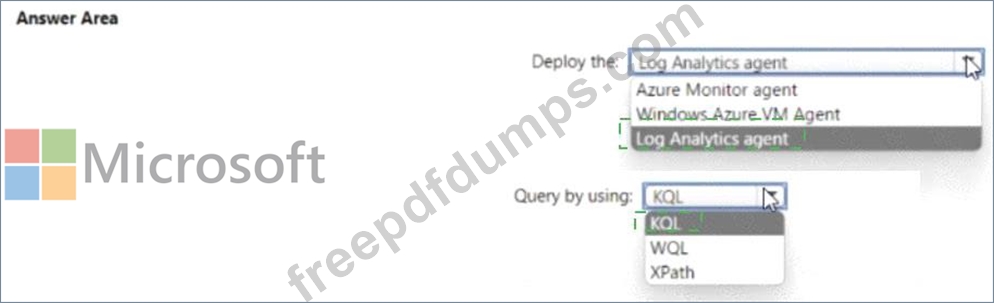
You need to meet the Microsoft Sentinel requirements for collecting Windows Security event logs. What should you do? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.


SC-200 Exam Question 65
You have a Microsoft Sentinel workspace.
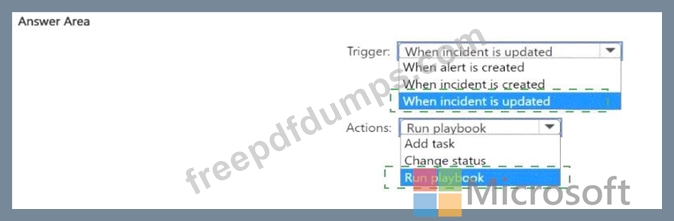
You need to configure the Fusion analytics rule to temporarily supress incidents generated by a Microsoft Defender connector. The solution must meet the following requirements:
* Minimize impact on the ability to detect multistage attacks.
* Minimize administrative effort.
How should you configure the rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to configure the Fusion analytics rule to temporarily supress incidents generated by a Microsoft Defender connector. The solution must meet the following requirements:
* Minimize impact on the ability to detect multistage attacks.
* Minimize administrative effort.
How should you configure the rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.