SC-200 Exam Question 11
You have a Microsoft 365 E5 subscription that contains two users named Userl and User2 and From the Copilot for Security portal, User1 starts a session and creates the following prompts:
* Prompt1: Provides access to the Entra plugin
* Prompt2: Provides access to the Intune plugin
* Prompt3: Provides access to the Entra plugin
User1 shares the session with User2.
User2 does NOT have access to Microsoft Intune.
For which prompts can User2 view results during the shared session?
* Prompt1: Provides access to the Entra plugin
* Prompt2: Provides access to the Intune plugin
* Prompt3: Provides access to the Entra plugin
User1 shares the session with User2.
User2 does NOT have access to Microsoft Intune.
For which prompts can User2 view results during the shared session?
SC-200 Exam Question 12
You have an Azure subscription that uses Microsoft Sentinel and contains 100 Linux virtual machines.
You need to monitor the virtual machines by using Microsoft Sentinel. The solution must meet the fallowing requirements:
* Minimize administrative effort
* Minimize the parsing required to read log data
What should you configure?
You need to monitor the virtual machines by using Microsoft Sentinel. The solution must meet the fallowing requirements:
* Minimize administrative effort
* Minimize the parsing required to read log data
What should you configure?
SC-200 Exam Question 13
You have a Microsoft Sentinel workspace that contains a custom workbook named Workbook1.
You need to create a visual based on the SecuntyEvent table. The solution must meet the following requirements:
* Identify the number of security events ingested during the past week.
* Display the count of events by day in a timechart
What should you add to Workbook1?
You need to create a visual based on the SecuntyEvent table. The solution must meet the following requirements:
* Identify the number of security events ingested during the past week.
* Display the count of events by day in a timechart
What should you add to Workbook1?
SC-200 Exam Question 14
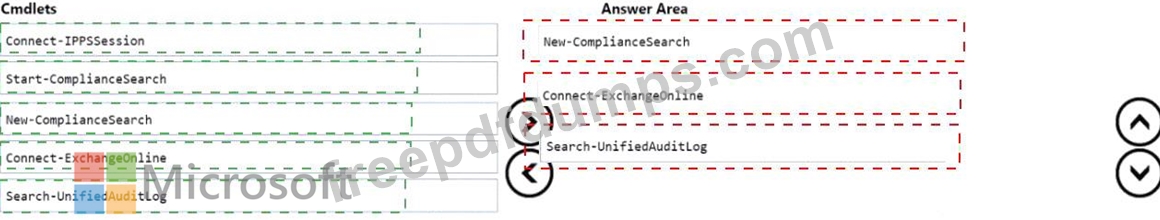
You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online.
You need to identify phishing email messages.
Which three cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
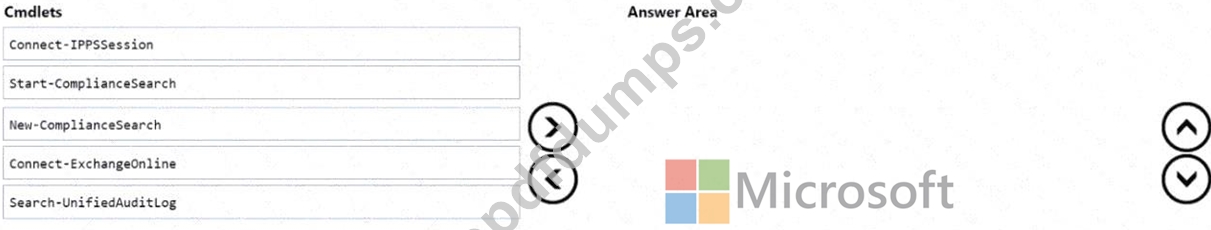
You need to identify phishing email messages.
Which three cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.

SC-200 Exam Question 15
You have the resources shown in the following table.

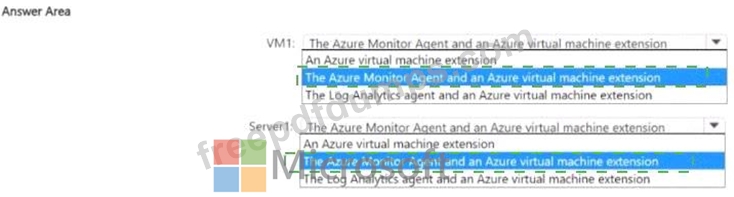
You have an Azure subscription that uses Mictosoft Defender for Cloud.
You need to use Defender for Cloud to protect VM1 and Server1. The solution must meet the following requirements:
* Support Advanced Threat Protection and vulnerability assessment
* Register each SQL Server 2022 instance as a SQL virtual machine.
* Minimize implementation and administrative effort
What should you deploy to each server? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
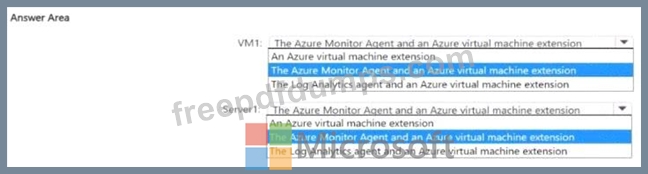

You have an Azure subscription that uses Mictosoft Defender for Cloud.
You need to use Defender for Cloud to protect VM1 and Server1. The solution must meet the following requirements:
* Support Advanced Threat Protection and vulnerability assessment
* Register each SQL Server 2022 instance as a SQL virtual machine.
* Minimize implementation and administrative effort
What should you deploy to each server? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.