SC-200 Exam Question 26
You have a Microsoft Sentinel workspace named SW1.
In SW1. you enable User and Entity Behavior Analytics (UEBA).
You need to use KQL to perform the following tasks:
* View the entity data that has fields for each type of entity.
* Assess the quality of rules by analyzing how well a rule performs.
Which table should you use in KQL for each task? To answer, drag the appropriate tables to the correct tasks.
Each table may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

In SW1. you enable User and Entity Behavior Analytics (UEBA).
You need to use KQL to perform the following tasks:
* View the entity data that has fields for each type of entity.
* Assess the quality of rules by analyzing how well a rule performs.
Which table should you use in KQL for each task? To answer, drag the appropriate tables to the correct tasks.
Each table may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

SC-200 Exam Question 27
You have an on-premises network.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Identity.
From the Microsoft Defender portal, you investigate an incident on a device named Device1 of a user named User1. The incident contains the following Defender for Identity alert.
Suspected identity theft (pass-the-ticket) (external ID 2018)
You need to contain the incident without affecting users and devices. The solution must minimize administrative effort.
What should you do?
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Identity.
From the Microsoft Defender portal, you investigate an incident on a device named Device1 of a user named User1. The incident contains the following Defender for Identity alert.
Suspected identity theft (pass-the-ticket) (external ID 2018)
You need to contain the incident without affecting users and devices. The solution must minimize administrative effort.
What should you do?
SC-200 Exam Question 28
You have an Azure subscription that use Microsoft Defender for Cloud and contains a user named User1.
You need to ensure that User1 can modify Microsoft Defender for Cloud security policies. The solution must use the principle of least privilege.
Which role should you assign to User1?
You need to ensure that User1 can modify Microsoft Defender for Cloud security policies. The solution must use the principle of least privilege.
Which role should you assign to User1?
SC-200 Exam Question 29
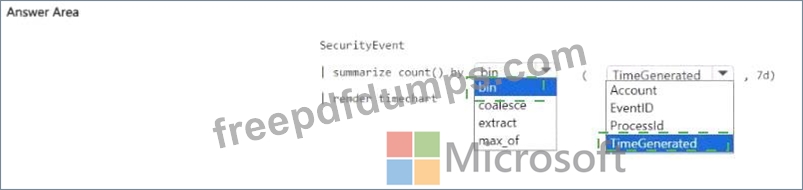
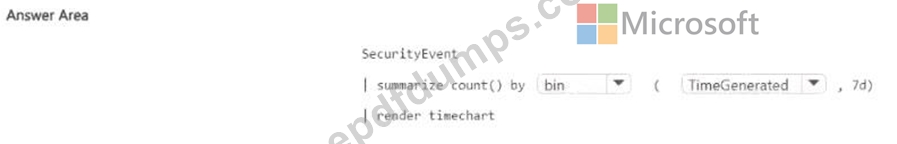
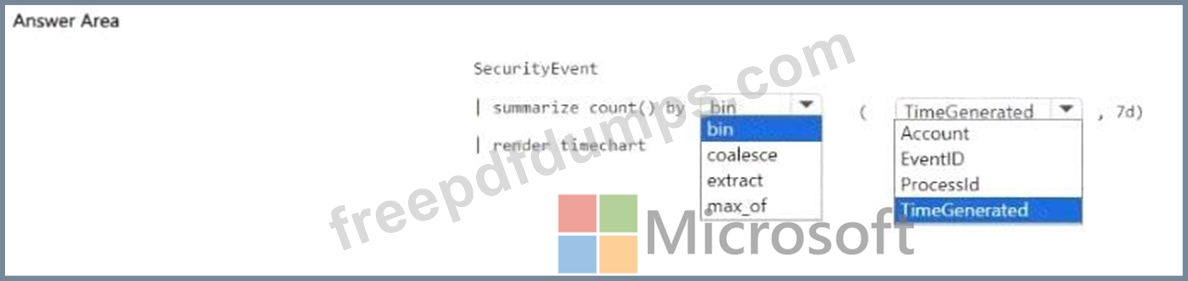
You have a Microsoft Sentinel workspace that contains a custom workbook.
You need to query for a summary of security events. The solution must meet the following requirements:
* Identify the number of security events ingested during the past week.
* Display the count of events by day in a chart.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to query for a summary of security events. The solution must meet the following requirements:
* Identify the number of security events ingested during the past week.
* Display the count of events by day in a chart.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-200 Exam Question 30
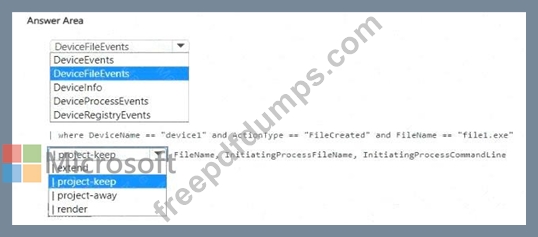
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR.
You discover a malicious process that was initiated by a file named File1exe on a device named Device1.
You need to create a KQL query that will identify when File1.exe was created. The solution must meet the following requirements:
* Return the FileName, InitiatingProcessFileName, and InitiatingProcessCommandLine columns.
* Minimize the volume of data returned.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You discover a malicious process that was initiated by a file named File1exe on a device named Device1.
You need to create a KQL query that will identify when File1.exe was created. The solution must meet the following requirements:
* Return the FileName, InitiatingProcessFileName, and InitiatingProcessCommandLine columns.
* Minimize the volume of data returned.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.