SC-400 Exam Question 6
You have a Microsoft 365 E5 tenant.
You need to create a custom trainable classifier that will detect product order forms. The solution must use the principle of least privilege.
What should you do first? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to create a custom trainable classifier that will detect product order forms. The solution must use the principle of least privilege.
What should you do first? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
SC-400 Exam Question 7
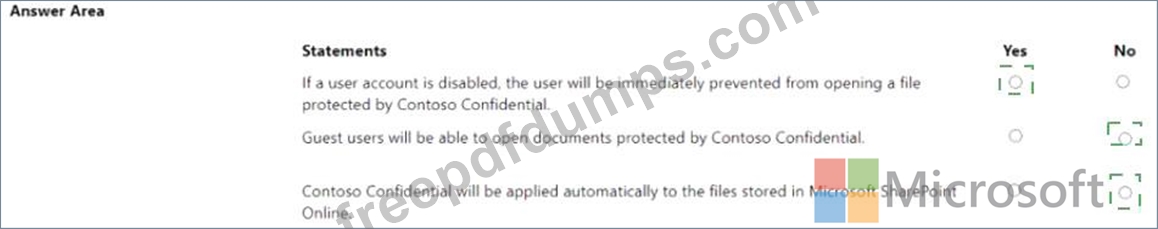
You have a Microsoft 365 subscription that contains a sensitivity label named Contoso Confidential.
You publish Contoso Confidential to all users.
Contoso Confidential is configured as shown in the Configuration exhibit. (Click the Configuration tab.) The Encryption settings of Contoso Confidential are configured as shown in the Encryption exhibit. (Click the Encryption tab.) For each of the following statements, select Yes if the statement is true Otherwise, select No NOTE: Each correct selection is worth one point
You publish Contoso Confidential to all users.
Contoso Confidential is configured as shown in the Configuration exhibit. (Click the Configuration tab.) The Encryption settings of Contoso Confidential are configured as shown in the Encryption exhibit. (Click the Encryption tab.) For each of the following statements, select Yes if the statement is true Otherwise, select No NOTE: Each correct selection is worth one point
SC-400 Exam Question 8
You have a Microsoft 365 E5 subscription that uses Microsoft Teams and contains a user named User1.
You configure Microsoft Purview Information Barriers.
You need to identify which information barrier policies apply to User1.
Which cmdlet should you use?
You configure Microsoft Purview Information Barriers.
You need to identify which information barrier policies apply to User1.
Which cmdlet should you use?
SC-400 Exam Question 9
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Data Classification service inspection method and send alerts as email.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Data Classification service inspection method and send alerts as email.
Does this meet the goal?
SC-400 Exam Question 10
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview compliance portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled Strue -AdminAuditLogCmdlets
"Mailbox" command.
Does that meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview compliance portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled Strue -AdminAuditLogCmdlets
"Mailbox" command.
Does that meet the goal?