NCM-MCI-5.15 Exam Question 21
An administrator is deploying a new application to a Nutanix Enterprise Cloud. The application requires a security to prevent unauthorized access. The application also uses many non-standard ports that are unique to it. Security should not be changed for existing applications.
What should the administrator do to meet these requirement?
What should the administrator do to meet these requirement?
NCM-MCI-5.15 Exam Question 22
An administrator receives an error indicating that the CVMs in the cluster are not syncing to any NTP servers.
An investigation of the issue finds:
* The NTP servers are configured in Prism
* The time on all CVMs is the same
* Both the CVMs and AHV hosts are configured for the UTC time zone
Which two steps can be taken to troubleshoot this issue? (Choose two.)
An investigation of the issue finds:
* The NTP servers are configured in Prism
* The time on all CVMs is the same
* Both the CVMs and AHV hosts are configured for the UTC time zone
Which two steps can be taken to troubleshoot this issue? (Choose two.)
NCM-MCI-5.15 Exam Question 23
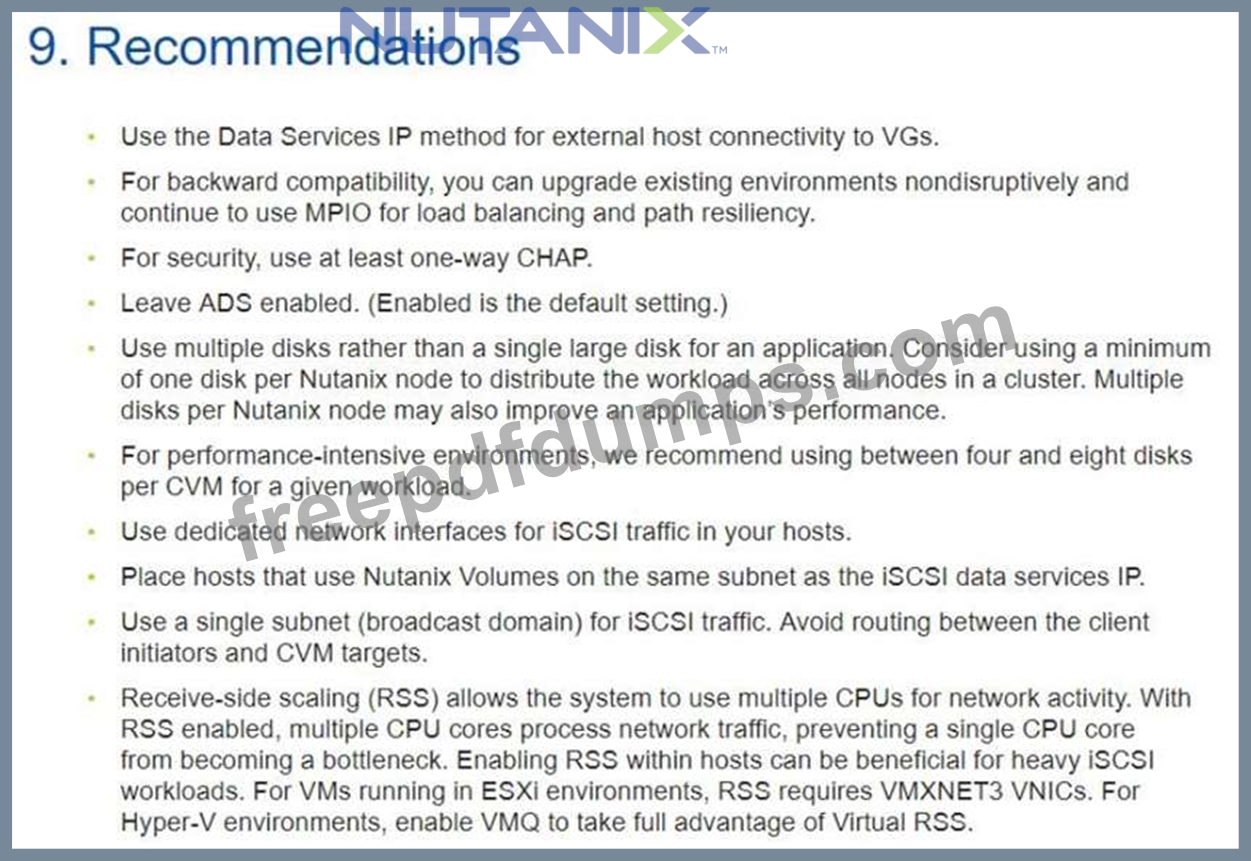
An administrator needs to deploy an application with a large amount of data connected via Nutanix Volumes.
Which two actions should the administrator take when designing the Volume Group? (Choose two.)
Which two actions should the administrator take when designing the Volume Group? (Choose two.)
NCM-MCI-5.15 Exam Question 24
An administrator needs to replace the self-signed certificate on a cluster. Which two requirements must be met as part of the process? (Choose two.)
NCM-MCI-5.15 Exam Question 25
In a Nutanix cluster, a Protection Domain contains 50 entities that are replicated to a remote Single Node Replication Target.
The current schedule configuration is as follows:
* Repeat every 6 hours
* Local Retention Policy 1
* Remote Retention Policy 8
* Starting time 12 am
At 8 am on Monday, the administrator discovers that a protected VM is corrupted. The latest good state was Sunday 2 pm. The administrator needs to maintain current protection.
Which strategy should the administrator use to meet these requirements?
The current schedule configuration is as follows:
* Repeat every 6 hours
* Local Retention Policy 1
* Remote Retention Policy 8
* Starting time 12 am
At 8 am on Monday, the administrator discovers that a protected VM is corrupted. The latest good state was Sunday 2 pm. The administrator needs to maintain current protection.
Which strategy should the administrator use to meet these requirements?