1Z0-888 Exam Question 101
Which two are considered good security practices when using passwords? (Choose two.)
1Z0-888 Exam Question 102
A crucial database, `db_prod', just disappeared from your production MySQL instance. In reviewing the available MySQL logs (General, Audit, or Slow) and your own application-level logs, you identified this command from a customer facing application:
SELECT id FROM users WHERE login='payback!';DROP DATABASE db_prod;' Which three methods could have been used to prevent this SQL injection attack from happening?
SELECT id FROM users WHERE login='payback!';DROP DATABASE db_prod;' Which three methods could have been used to prevent this SQL injection attack from happening?
1Z0-888 Exam Question 103
Consider the index information for the dept_emp table in the employee's schema:
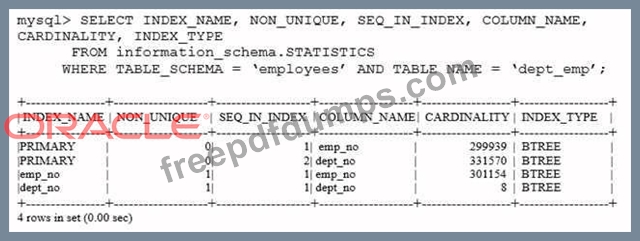
Which two conclusions can be made based on the output of the query?

Which two conclusions can be made based on the output of the query?
1Z0-888 Exam Question 104
Exhibit:

What does the possible_keys column in this output denote?

What does the possible_keys column in this output denote?
1Z0-888 Exam Question 105
After analysis on the slow query log on a high-end OLTP service, the table identified in the slow queries is:
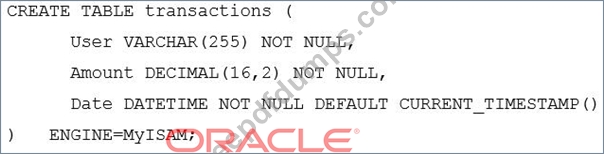
What are the two most likely reasons for the slowness given this output? (Choose two.)

What are the two most likely reasons for the slowness given this output? (Choose two.)

