200-201 Exam Question 121
What is a difference between tampered and untampered disk images?
200-201 Exam Question 122
Refer to the exhibit.
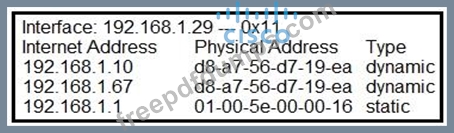
What is occurring in this network?

What is occurring in this network?
200-201 Exam Question 123
Refer to the exhibit.

In which Linux log file is this output found?

In which Linux log file is this output found?
200-201 Exam Question 124
Which utility blocks a host portscan?
200-201 Exam Question 125
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?

