300-215 Exam Question 11
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
300-215 Exam Question 12
Refer to the exhibit.
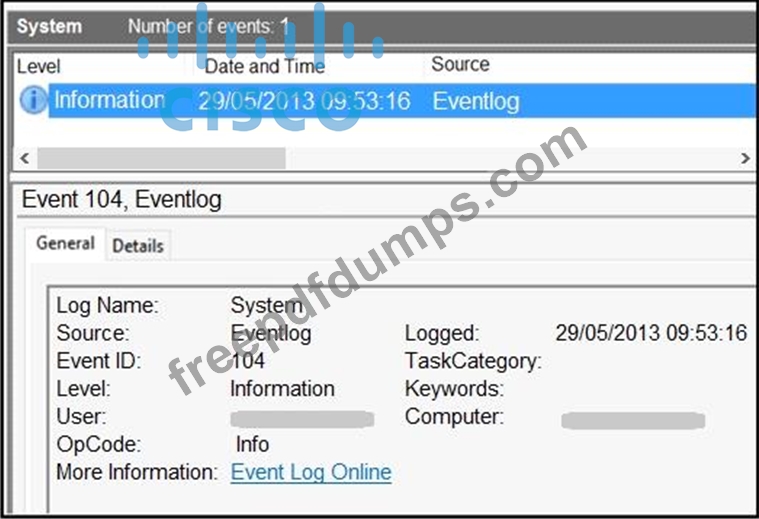
An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?

An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
300-215 Exam Question 13
An attacker embedded a macro within a word processing file opened by a user in an organization's legal department. The attacker used this technique to gain access to confidential financial dat a. Which two recommendations should a security expert make to mitigate this type of attack? (Choose two.)
300-215 Exam Question 14
An incident response team is recommending changes after analyzing a recent compromise in which:
a large number of events and logs were involved;
team members were not able to identify the anomalous behavior and escalate it in a timely manner; several network systems were affected as a result of the latency in detection; security engineers were able to mitigate the threat and bring systems back to a stable state; and the issue reoccurred shortly after and systems became unstable again because the correct information was not gathered during the initial identification phase.
Which two recommendations should be made for improving the incident response process? (Choose two.)
a large number of events and logs were involved;
team members were not able to identify the anomalous behavior and escalate it in a timely manner; several network systems were affected as a result of the latency in detection; security engineers were able to mitigate the threat and bring systems back to a stable state; and the issue reoccurred shortly after and systems became unstable again because the correct information was not gathered during the initial identification phase.
Which two recommendations should be made for improving the incident response process? (Choose two.)
300-215 Exam Question 15
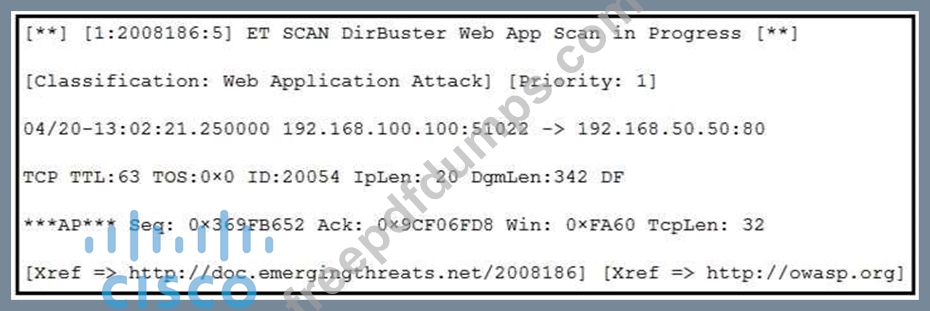
Refer to the exhibit. According to the SNORT alert, what is the attacker performing?

