300-215 Exam Question 16
A network host is infected with malware by an attacker who uses the host to make calls for files and shuttle traffic to bots. This attack went undetected and resulted in a significant loss. The organization wants to ensure this does not happen in the future and needs a security solution that will generate alerts when command and control communication from an infected device is detected. Which network security solution should be recommended?
300-215 Exam Question 17
Refer to the exhibit.
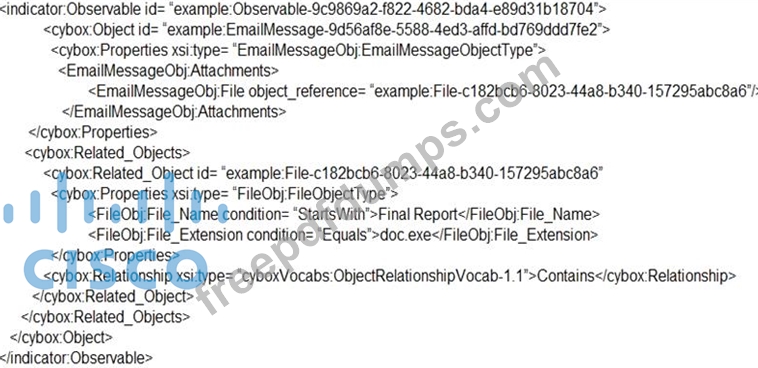
Which determination should be made by a security analyst?

Which determination should be made by a security analyst?
300-215 Exam Question 18
Refer to the exhibit.
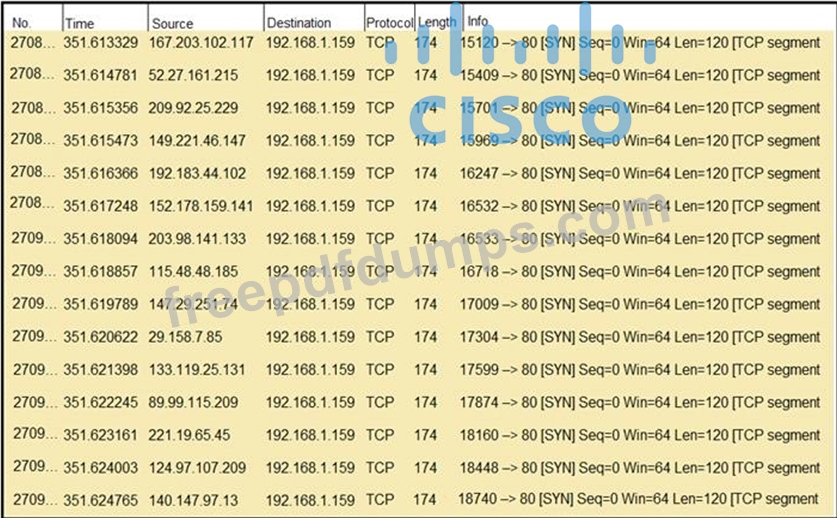
What should an engineer determine from this Wireshark capture of suspicious network traffic?

What should an engineer determine from this Wireshark capture of suspicious network traffic?
300-215 Exam Question 19
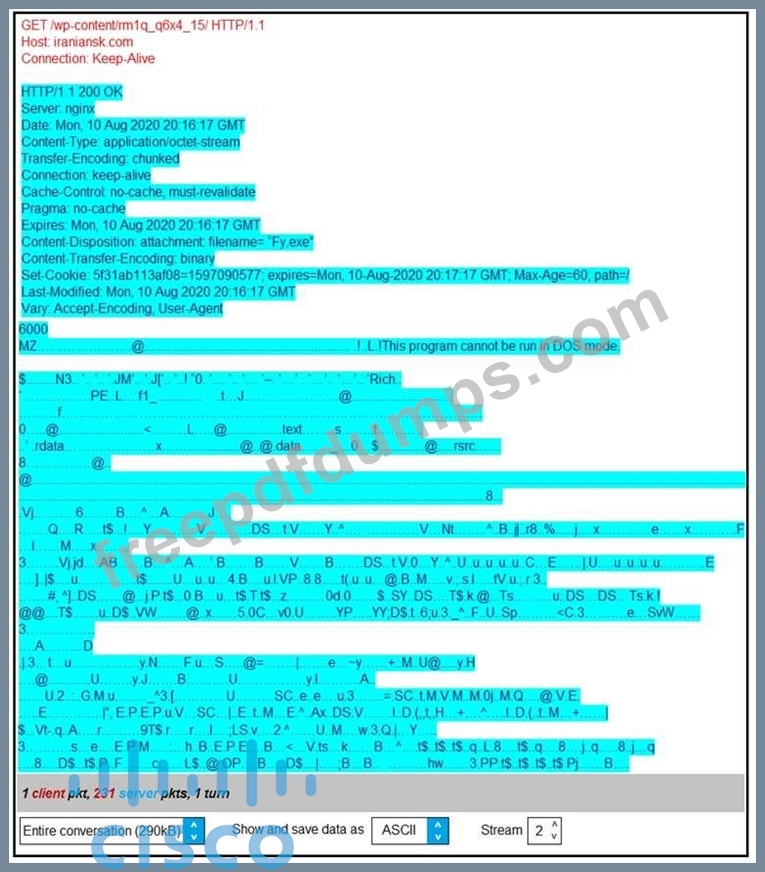
Refer to the exhibit. According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)
300-215 Exam Question 20
An organization recovered from a recent ransomware outbreak that resulted in significant business damage. Leadership requested a report that identifies the problems that triggered the incident and the security team's approach to address these problems to prevent a reoccurrence. Which components of the incident should an engineer analyze first for this report?

