300-215 Exam Question 26
Refer to the exhibit.
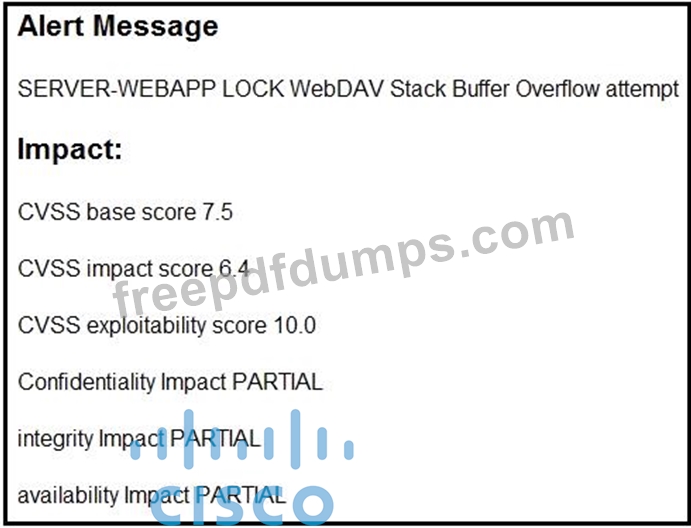
After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business critical, web-based application and violated its availability. Which two migration techniques should the engineer recommend? (Choose two.)

After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business critical, web-based application and violated its availability. Which two migration techniques should the engineer recommend? (Choose two.)
300-215 Exam Question 27
Refer to the exhibit.
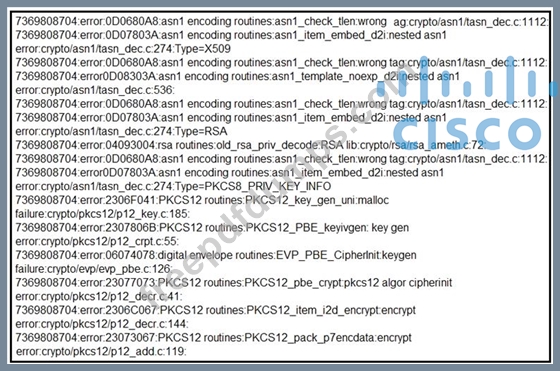
What should be determined from this Apache log?

What should be determined from this Apache log?
300-215 Exam Question 28
Which tool conducts memory analysis?
300-215 Exam Question 29
Refer to the exhibit.

Which two determinations should be made about the attack from the Apache access logs? (Choose two.)

Which two determinations should be made about the attack from the Apache access logs? (Choose two.)

