350-201 Exam Question 1
Refer to the exhibit.
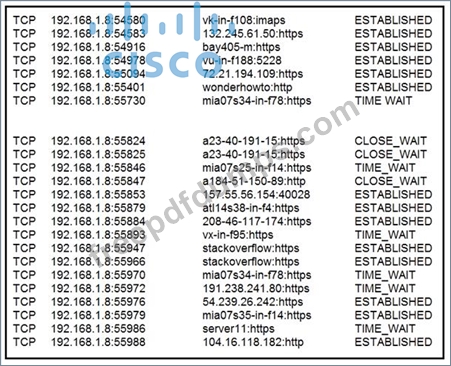
A security analyst needs to investigate a security incident involving several suspicious connections with a possible attacker. Which tool should the analyst use to identify the source IP of the offender?

A security analyst needs to investigate a security incident involving several suspicious connections with a possible attacker. Which tool should the analyst use to identify the source IP of the offender?
350-201 Exam Question 2
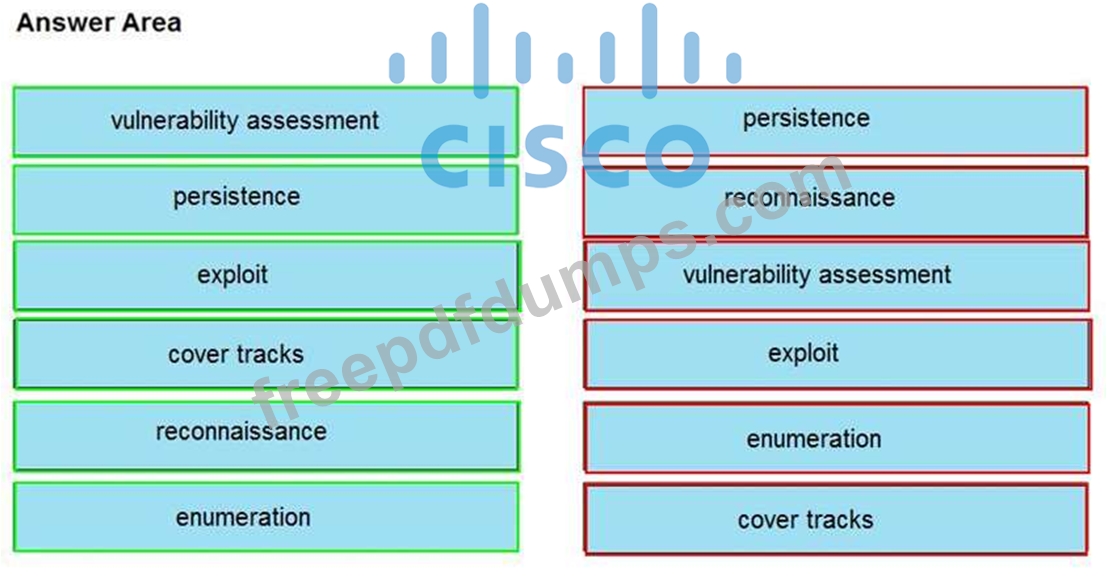
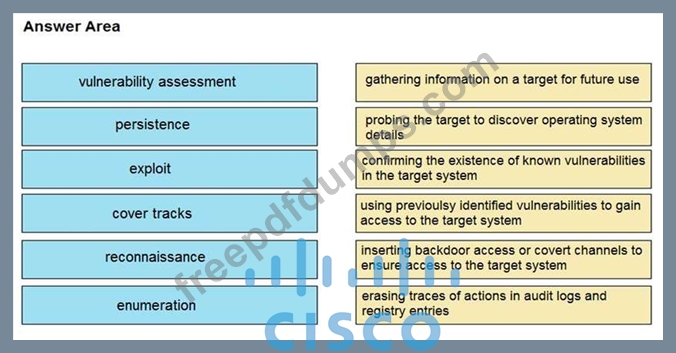
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.

350-201 Exam Question 3
A SOC team is investigating a recent, targeted social engineering attack on multiple employees. Cross- correlated log analysis revealed that two hours before the attack, multiple assets received requests on TCP port 79. Which action should be taken by the SOC team to mitigate this attack?
350-201 Exam Question 4
A company recently started accepting credit card payments in their local warehouses and is undergoing a PCI audit. Based on business requirements, the company needs to store sensitive authentication data for 45 days. How must data be stored for compliance?
350-201 Exam Question 5
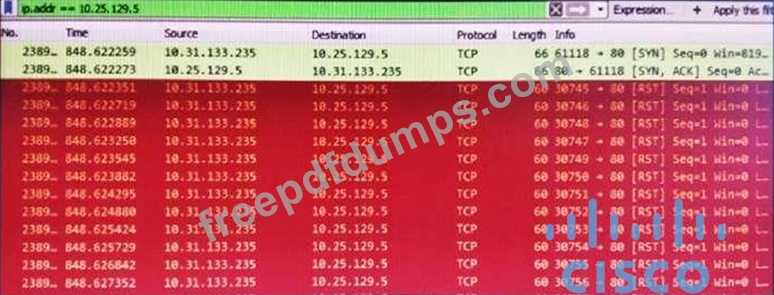
Refer to the exhibit. What is occurring in this packet capture?