350-201 Exam Question 6
How is a SIEM tool used?
350-201 Exam Question 7
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days.
Having the names of the 3 destination countries and the user's working hours, what must the analyst do next to detect an abnormal behavior?
Having the names of the 3 destination countries and the user's working hours, what must the analyst do next to detect an abnormal behavior?
350-201 Exam Question 8
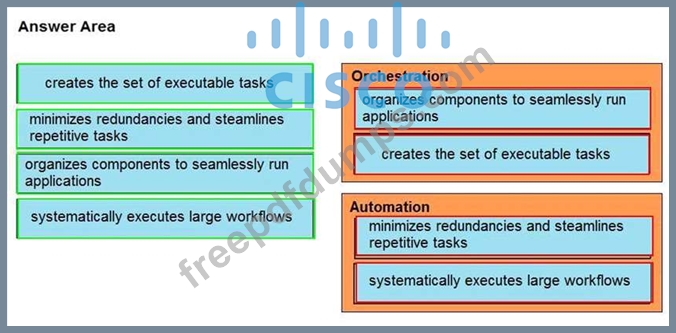
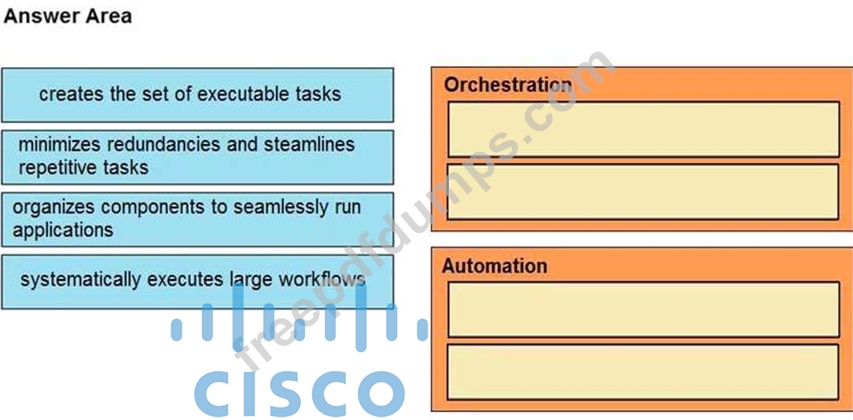
Drag and drop the function on the left onto the mechanism on the right.

350-201 Exam Question 9
A security architect in an automotive factory is working on the Cyber Security Management System and is implementing procedures and creating policies to prevent attacks. Which standard must the architect apply?
350-201 Exam Question 10
Refer to the exhibit.
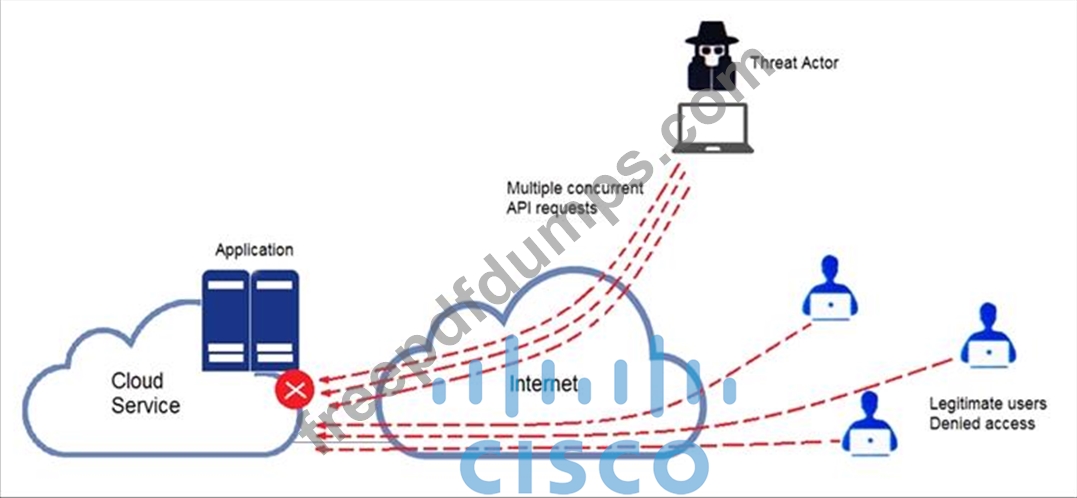
A threat actor behind a single computer exploited a cloud-based application by sending multiple concurrent API requests. These requests made the application unresponsive. Which solution protects the application from being overloaded and ensures more equitable application access across the end-user community?

A threat actor behind a single computer exploited a cloud-based application by sending multiple concurrent API requests. These requests made the application unresponsive. Which solution protects the application from being overloaded and ensures more equitable application access across the end-user community?