CS0-002 Exam Question 76
During an Incident, it Is determined that a customer database containing email addresses, first names, and last names was exfiltrated. Which ot the following should the security analyst do NEXT?
CS0-002 Exam Question 77
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has received the following output from the latest scan:
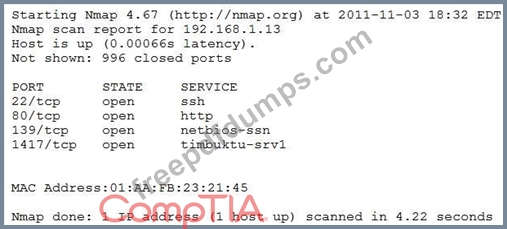
The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?

The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?
CS0-002 Exam Question 78
An analyst reviews the most recent vulnerability management report and notices a firewall with 99.98% required uptime is reporting different firmware versions on scans than were reported in previous scans. The vendor released new firewall firmware a few months ago. Which of the following will the analyst most likely do next given the requirements?
CS0-002 Exam Question 79
A security analyst is investigating an incident that appears to have started with SOL injection against a publicly available web application. Which of the following is the FIRST step the analyst should take to prevent future attacks?
CS0-002 Exam Question 80
An organization has a policy prohibiting remote administration of servers where web services are running.
One of the Nmap scans is shown here:
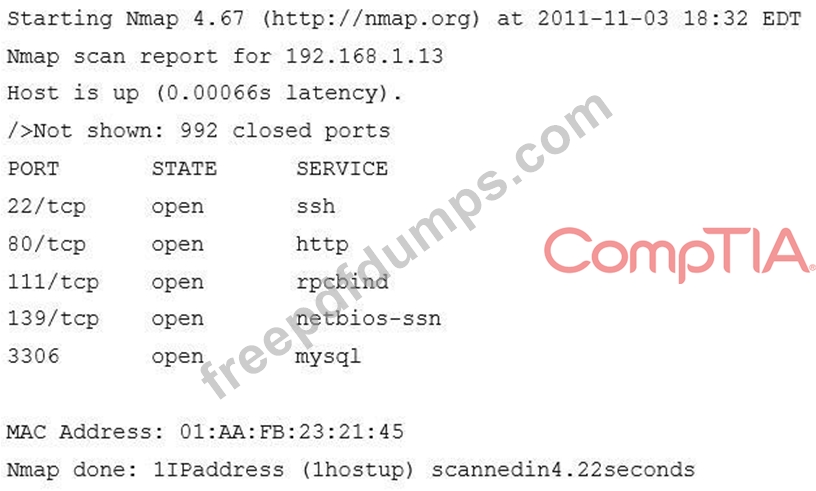
Given the organization's policy, which of the following services should be disabled on this server?
One of the Nmap scans is shown here:

Given the organization's policy, which of the following services should be disabled on this server?

