CS0-002 Exam Question 86
A security analyst is reviewing a firewall usage report that contains traffic generated over the last 30 minutes in order to locate unusual traffic patterns:
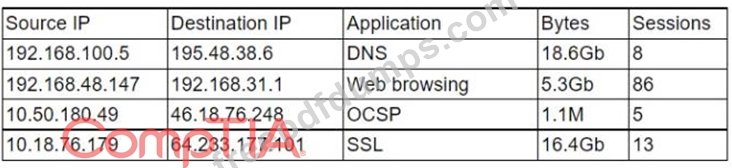
Which of the following source IP addresses does the analyst need to investigate further?

Which of the following source IP addresses does the analyst need to investigate further?
CS0-002 Exam Question 87
Which of the following is the primary reason financial institutions may share up-to-date threat intelligence information on a secure feed that is dedicated to their sector?
CS0-002 Exam Question 88
An organization that uses SPF has been notified emails sent via its authorized third-party partner are getting rejected A security analyst reviews the DNS entry and sees the following:
v=spf1 ip4:180.10.6.5 ip4:180.10.6.10 include:robustmail.com -all
The organization's primary mail server IP is 180.10 6.6, and the secondary mail server IP is 180.10.6.5. The organization's third-party mail provider is "Robust Mail" with the domain name robustmail.com.
Which of the following is the MOST likely reason for the rejected emails?
v=spf1 ip4:180.10.6.5 ip4:180.10.6.10 include:robustmail.com -all
The organization's primary mail server IP is 180.10 6.6, and the secondary mail server IP is 180.10.6.5. The organization's third-party mail provider is "Robust Mail" with the domain name robustmail.com.
Which of the following is the MOST likely reason for the rejected emails?
CS0-002 Exam Question 89
The majority of a company's employees have stated they are unable to perform their job duties due to outdated workstations, so the company has decided to institute BYOD. Which of the following would a security analyst MOST likely recommend for securing the proposed solution?
CS0-002 Exam Question 90
An application developer needs help establishing a digital certificate for a new application. Which of the following illustrates a certificate management best practice?

