CS0-002 Exam Question 96
industry partners from critical infrastructure organizations were victims of attacks on their SCADA devices.
The attacks used privilege escalation to gain access to SCADA administration and access management solutions would help to mitigate this risk?
The attacks used privilege escalation to gain access to SCADA administration and access management solutions would help to mitigate this risk?
CS0-002 Exam Question 97
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following:
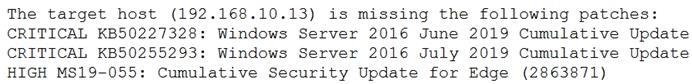
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Tool A reported the following:

Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
CS0-002 Exam Question 98
A newly discovered malware has a known behavior of connecting outbound to an external destination on port 27500 for the purpose of exfiltrating data. The following are four snippets taken from running netstat -anon separate Windows workstations:
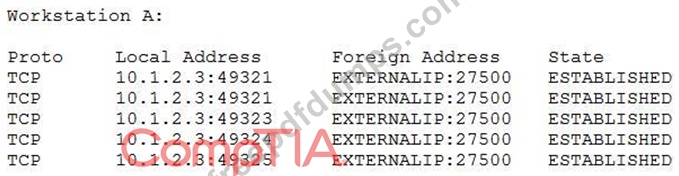


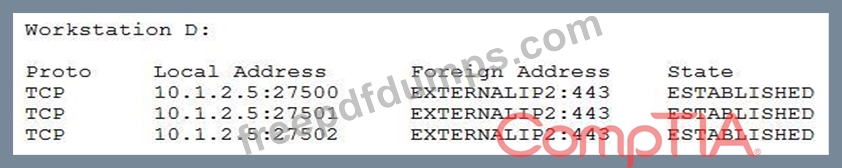
Based on the above information, which of the following is MOST likely to be exposed to this malware?




Based on the above information, which of the following is MOST likely to be exposed to this malware?
CS0-002 Exam Question 99
A company's security team recently discovered a number of workstations that are at the end of life. The workstation vendor informs the team that the product is no longer supported and patches are no longer available The company is not prepared to cease its use of these workstations Which of the following would be the BEST method to protect these workstations from threats?
CS0-002 Exam Question 100
A vulnerability assessment solution is hosted in the cloud This solution will be used as an accurate inventory data source for both the configuration management database and the governance nsk and compliance tool An analyst has been asked to automate the data acquisition Which of the following would be the BEST way to acqutre the data'

