CS0-002 Exam Question 166
An organization discovers motherboards within the environment that appear to have been physically altered during the manufacturing process. Which of the following is the BEST course of action to mitigate the risk of this reoccurring?
CS0-002 Exam Question 167
Industry partners from critical infrastructure organizations were victims of attacks on their SCADA devices. The attacker was able to gain access to the SCADA by logging in to an account with weak credentials. Which of the following identity and access management solutions would help to mitigate this risk?
CS0-002 Exam Question 168
During routine monitoring a security analyst identified the following enterpnse network traffic:
Packet capture output:
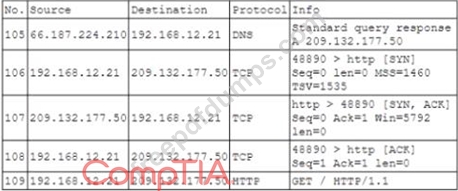
Which of the following BEST describes what the security analyst observed?
Packet capture output:

Which of the following BEST describes what the security analyst observed?
CS0-002 Exam Question 169
A security manager has asked an analyst to provide feedback on the results of a penetration test. After reviewing the results, the manager requests information regarding the possible exploitation of vulnerabilities. Which of the following information data points would be MOST useful for the analyst to provide to the security manager, who would then communicate the risk factors to the senior management team? (Select TWO).
CS0-002 Exam Question 170
A technician receives the following security alert from the firewall's automated system:
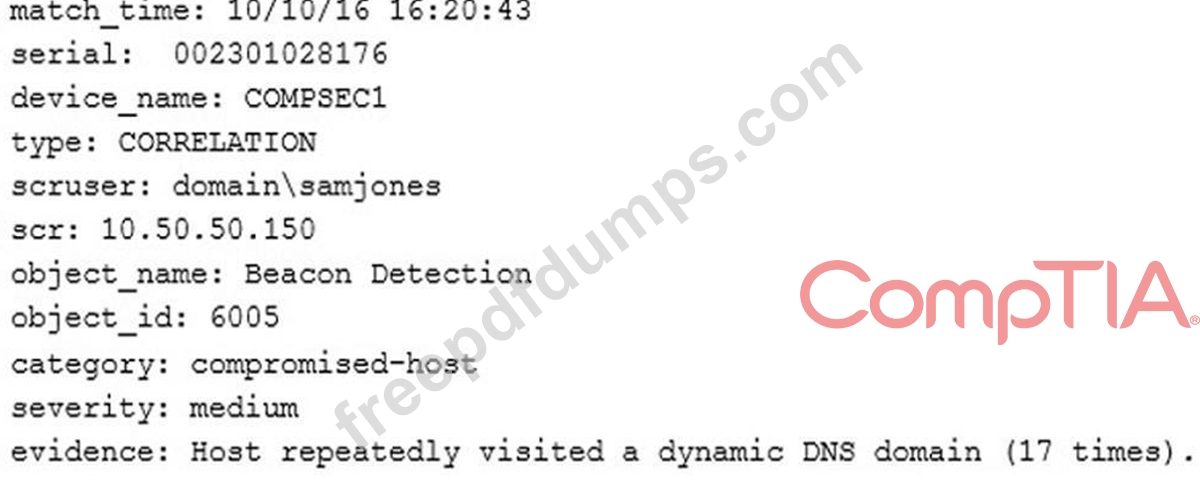
After reviewing the alert, which of the following is the BEST analysis?

After reviewing the alert, which of the following is the BEST analysis?

