CS0-002 Exam Question 156
A red team actor observes it is common practice to allow cell phones to charge on company computers, but access to the memory storage is blocked. Which of the following are common attack techniques that take advantage of this practice? (Choose two.)
CS0-002 Exam Question 157
Review the following results:
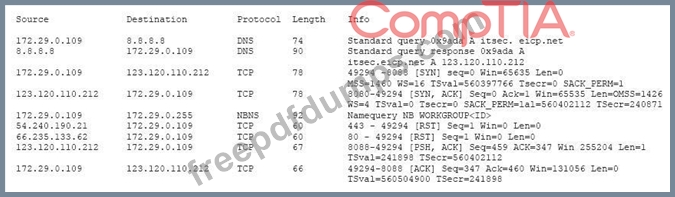
Which of the following has occurred?

Which of the following has occurred?
CS0-002 Exam Question 158
A security analyst is reviewing the following web server log:
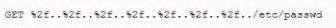
Which of the following BEST describes the issue?
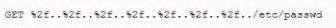
Which of the following BEST describes the issue?
CS0-002 Exam Question 159
A security analyst positively identified the threat, vulnerability, and remediation. The analyst is ready to implement the corrective control. Which of the following would be the MOST inhibiting to applying the fix?
CS0-002 Exam Question 160
A company has a cluster of web servers that is critical to the business. A systems administrator installed a utility to troubleshoot an issue, and the utility caused the entire cluster to 90 offline. Which of the following solutions would work BEST prevent to this from happening again?

