CS0-002 Exam Question 141
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output:
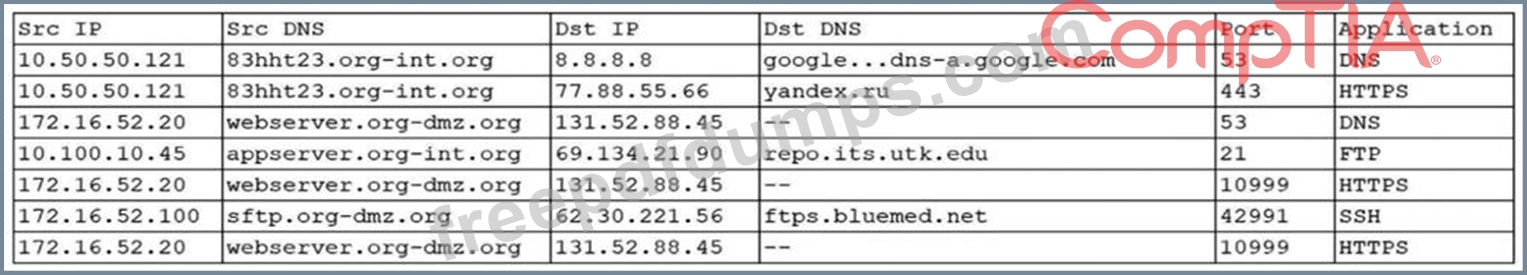
Which of the following should be the focus of the investigation?

Which of the following should be the focus of the investigation?
CS0-002 Exam Question 142
A Chief Information Security Officer (CISO) is concerned developers have too much visibility into customer dat
a. Which of the following controls should be implemented to BEST address these concerns?
a. Which of the following controls should be implemented to BEST address these concerns?
CS0-002 Exam Question 143
A vulnerability analyst needs to identify all systems with unauthorized web servers on the
10.1.1.0/24 network. The analyst uses the following default Nmap scan:
nmap -sV -p 1-65535 10.1.1.0/24
Which of the following would be the result of running the above command?
10.1.1.0/24 network. The analyst uses the following default Nmap scan:
nmap -sV -p 1-65535 10.1.1.0/24
Which of the following would be the result of running the above command?
CS0-002 Exam Question 144
A company's marketing emails are either being found in a spam folder or not being delivered at all. The security analyst investigates the issue and discovers the emails in question are being sent on behalf of the company by a third party in1marketingpartners.com Below is the exiting SPP word:

Which of the following updates to the SPF record will work BEST to prevent the emails from being marked as spam or blocked?
A)

B)

C)

D)
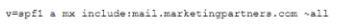

Which of the following updates to the SPF record will work BEST to prevent the emails from being marked as spam or blocked?
A)

B)

C)

D)
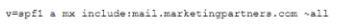
CS0-002 Exam Question 145
After examine a header and footer file, a security analyst begins reconstructing files by scanning the raw data bytes of a hard disk and rebuilding them. Which of the following techniques is the analyst using?

