SYO-501 Exam Question 31
An organization's internal auditor discovers that large sums of money have recently been paid to a vendor that management does not recognize. The IT security department is asked to investigate the organizations the organization's ERP system to determine how the accounts payable module has been used to make these vendor payments.
The IT security department finds the following security configuration for the accounts payable module:
* New Vendor Entry - Required Role: Accounts Payable Clerk
* New Vendor Approval - Required Role: Accounts Payable Clerk
* Vendor Payment Entry - Required Role: Accounts Payable Clerk
* Vendor Payment Approval - Required Role: Accounts Payable Manager
Which of the following changes to the security configuration of the accounts payable module would BEST mitigate the risk?

The IT security department finds the following security configuration for the accounts payable module:
* New Vendor Entry - Required Role: Accounts Payable Clerk
* New Vendor Approval - Required Role: Accounts Payable Clerk
* Vendor Payment Entry - Required Role: Accounts Payable Clerk
* Vendor Payment Approval - Required Role: Accounts Payable Manager
Which of the following changes to the security configuration of the accounts payable module would BEST mitigate the risk?

SYO-501 Exam Question 32
An administrator is beginning an authorized penetration test of a corporate network. Which of the following tools would BEST assist in identifying potential attacks?
SYO-501 Exam Question 33
DRAG DROP
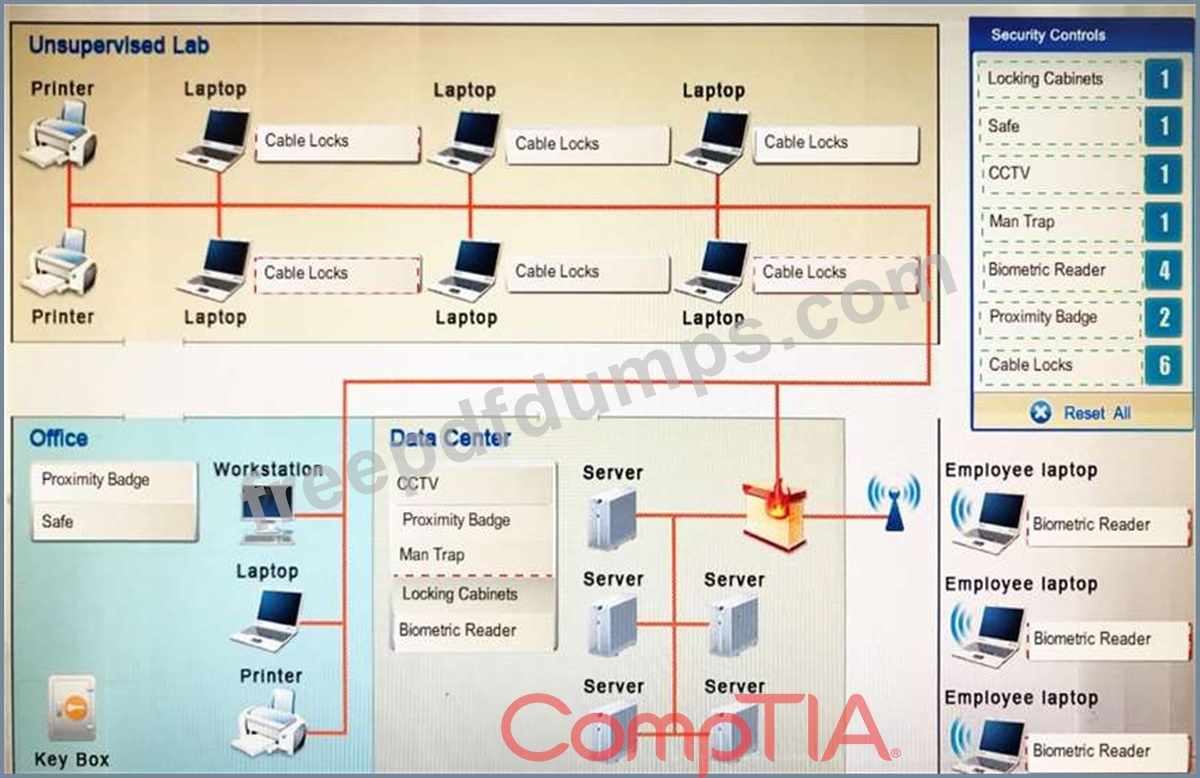
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.
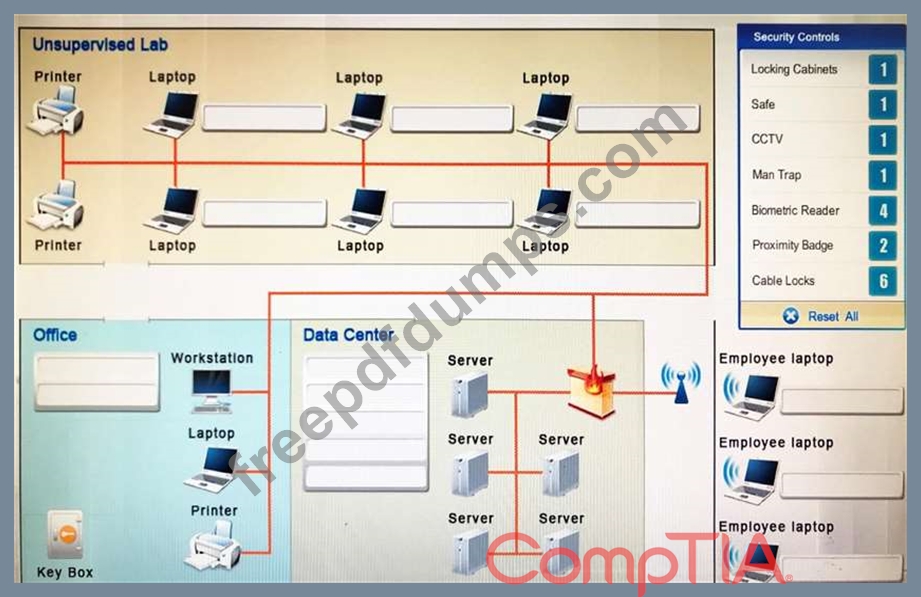
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.

SYO-501 Exam Question 34
A security administrator receives an alert from a third-party vendor that indicates a certificate that was installed in the browser has been hijacked at the root of a small public CA. The security administrator knows there are at least four different browsers in use on more than a thousand computers in the domain worldwide.
Which of the following solutions would be BEST for the security administrator to implement to most efficiently assist with this issue?
Which of the following solutions would be BEST for the security administrator to implement to most efficiently assist with this issue?
SYO-501 Exam Question 35
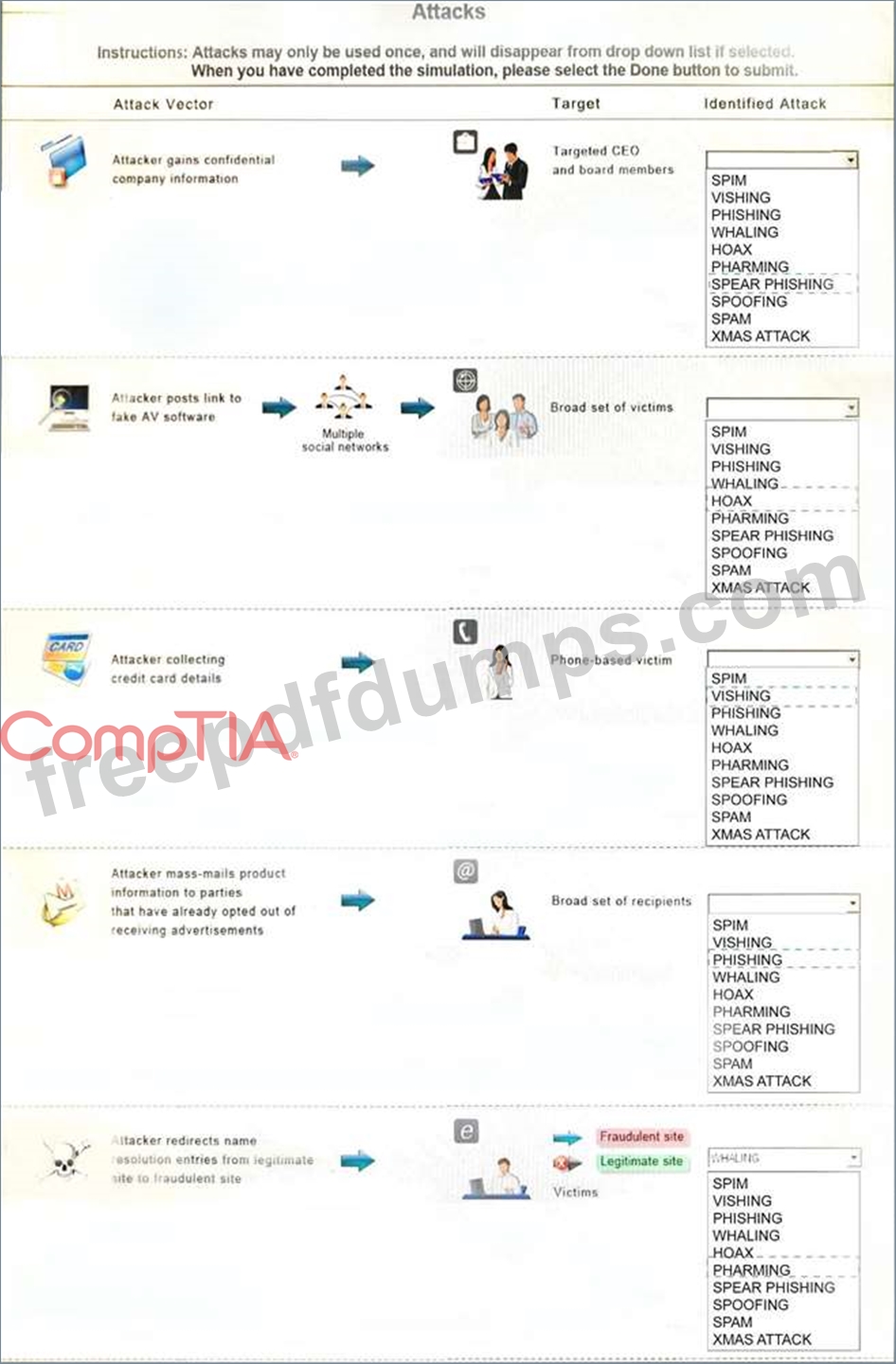
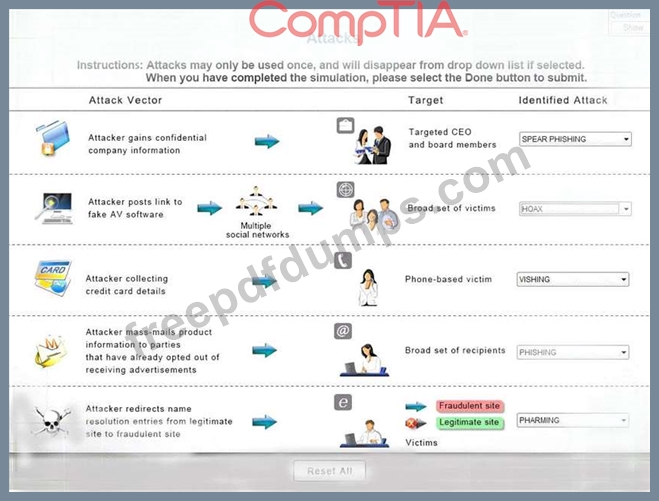
Select the appropriate attack from each drop down list to label the corresponding illustrated attack.
Instructions: Attacks may only be used once, and will disappear from drop down list if selected. When you have completed the simulation, please select the Done button to submit.
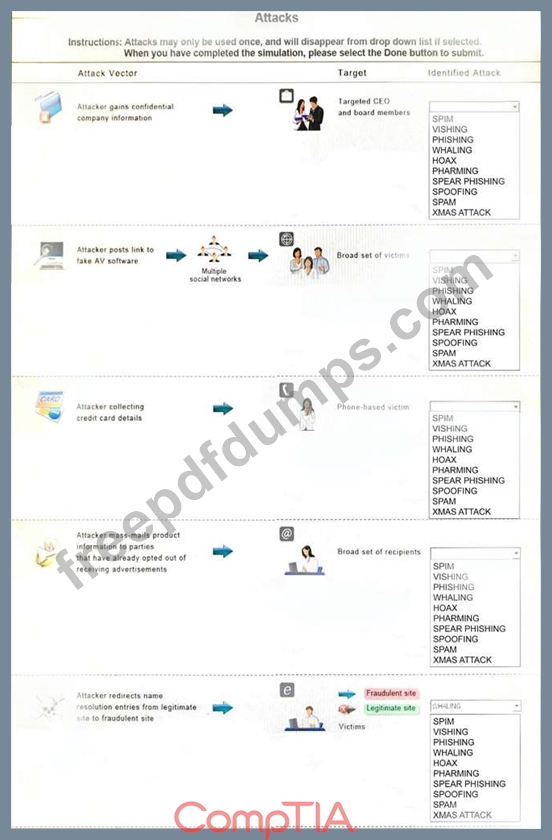
Instructions: Attacks may only be used once, and will disappear from drop down list if selected. When you have completed the simulation, please select the Done button to submit.