SYO-501 Exam Question 11
DRAG DROP
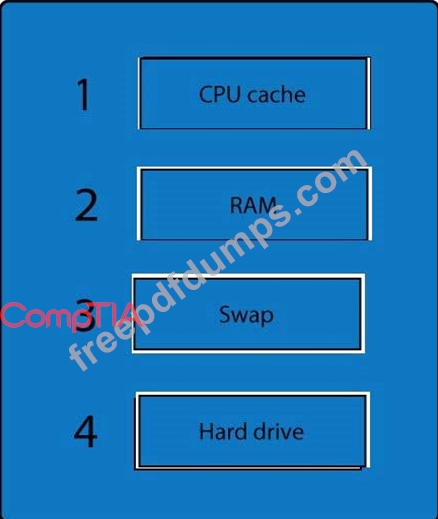
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.
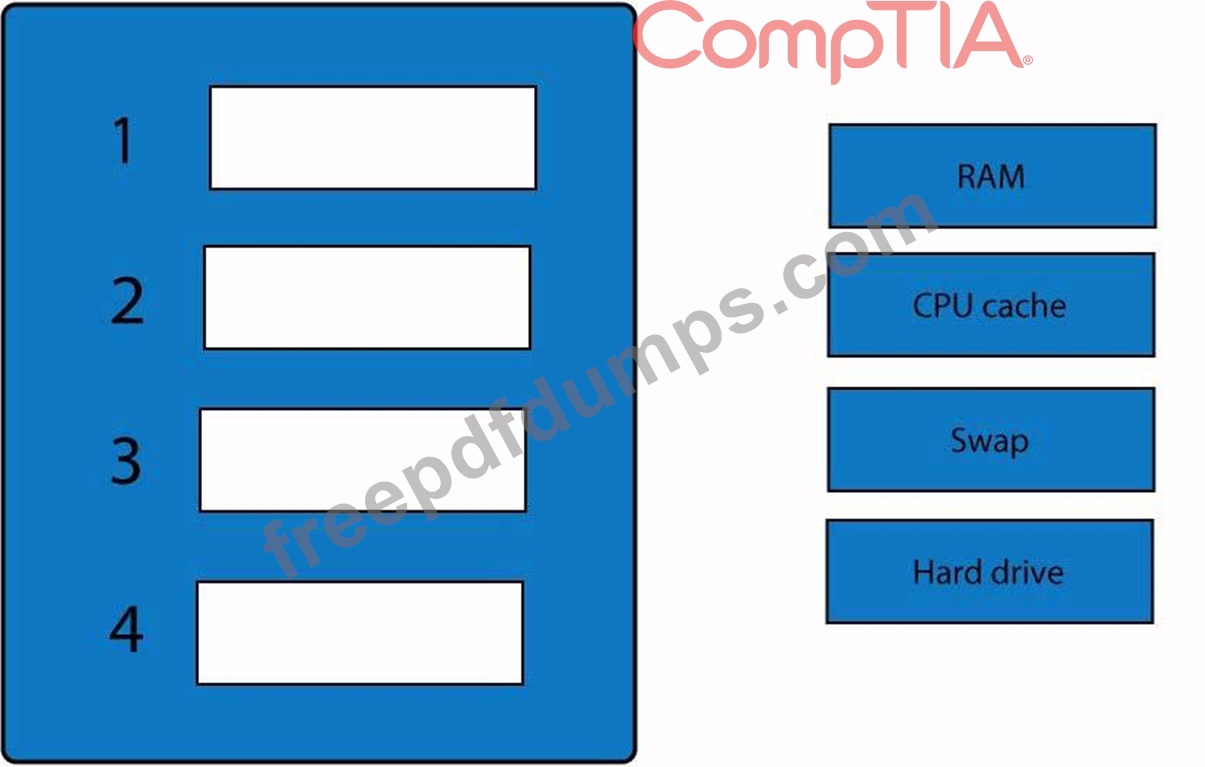
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.

SYO-501 Exam Question 12
A NIPS administrator needs to install a new signature to observe the behavior of a worm that may be spreading over SMB Which of the following signatures should be installed on the NIPS'?
SYO-501 Exam Question 13
A security analyst runs a monthly file integrity check on the main web server. When analyzing the logs, the analyst observed the following entry:
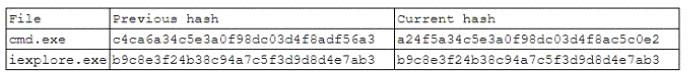
No OS patches were applied to this server during this period. Considering the log output, which of the following is the BEST conclusion?

No OS patches were applied to this server during this period. Considering the log output, which of the following is the BEST conclusion?
SYO-501 Exam Question 14
A user clicked an email link that led to a website than infected the workstation with a virus. The virus
encrypted all the network shares to which the user had access. The virus was not deleted or blocked by
the company's email filter, website filter, or antivirus. Which of the following describes what occurred?
encrypted all the network shares to which the user had access. The virus was not deleted or blocked by
the company's email filter, website filter, or antivirus. Which of the following describes what occurred?
SYO-501 Exam Question 15
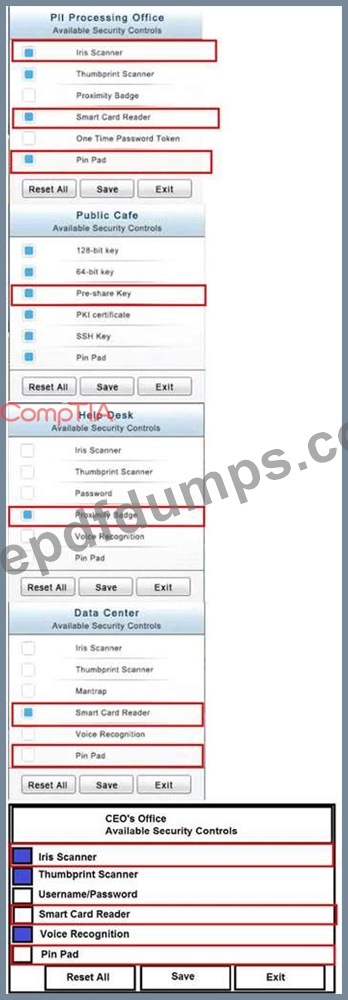
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.
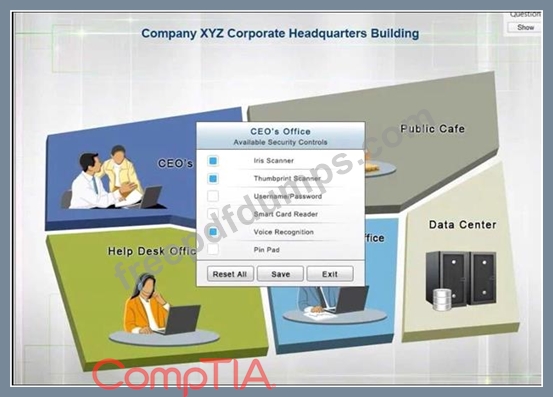
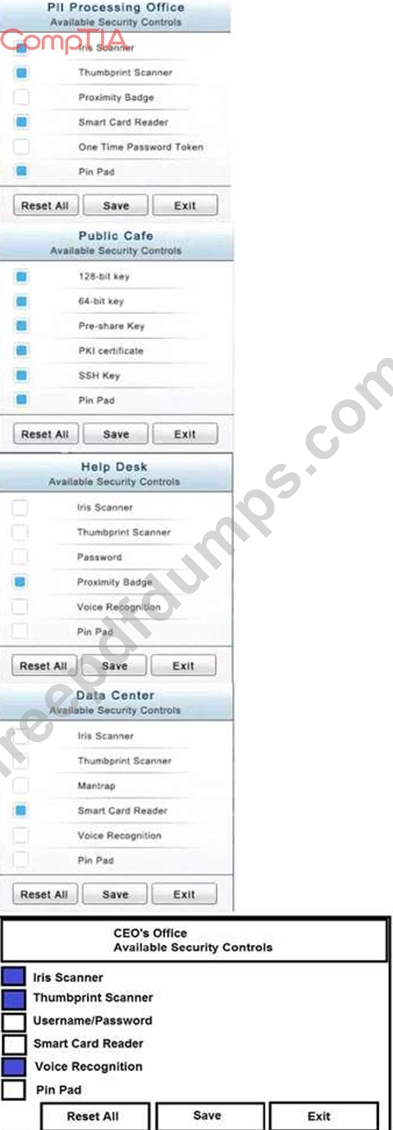
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.