CS0-002 Exam Question 11
A development team uses open-source software and follows an Agile methodology with two-week sprints. Last month, the security team filed a bug for an insecure version of a common library.
The DevOps team updated the library on the server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security team found the same vulnerability on the server.
Which of the following should be done to correct the cause of the vulnerability?
The DevOps team updated the library on the server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security team found the same vulnerability on the server.
Which of the following should be done to correct the cause of the vulnerability?
CS0-002 Exam Question 12
Which of the following describes why it is important to include scope within the rules of engagement of a penetration test?
CS0-002 Exam Question 13
A security analyst receives an alert that highly sensitive information has left the company's network Upon investigation, the analyst discovers an outside IP range has had connections from three servers more than 100 times m the past month.
The affected servers are virtual machines.
Which of the following is the BEST course of action?
The affected servers are virtual machines.
Which of the following is the BEST course of action?
CS0-002 Exam Question 14
An analyst is reviewing the following code output of a vulnerability scan:
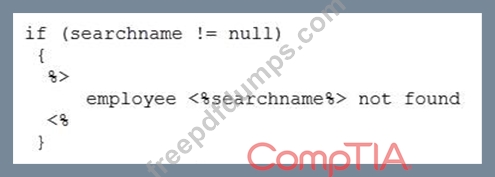
Which of the following types of vulnerabilities does this MOST likely represent?

Which of the following types of vulnerabilities does this MOST likely represent?
CS0-002 Exam Question 15
A large software company wants to move as source control and deployment pipelines into a cloud-computing environment. Due to the nature of the business management determines the recovery time objective needs to be within one hour. Which of the following strategies would put the company in the BEST position to achieve the desired recovery time?

