CS0-002 Exam Question 21
Which of the following technologies can be used to house the entropy keys for task encryption on desktops and laptops?
CS0-002 Exam Question 22
An HR employee began having issues with a device becoming unresponsive after attempting to open an email attachment. When informed, the security analyst became suspicious of the situation, even though there was not any unusual behavior on the IDS or any alerts from the antivirus software.
Which of the following BEST describes the type of threat in this situation?
Which of the following BEST describes the type of threat in this situation?
CS0-002 Exam Question 23
During a recent audit, there were a lot of findings similar to and including the following:
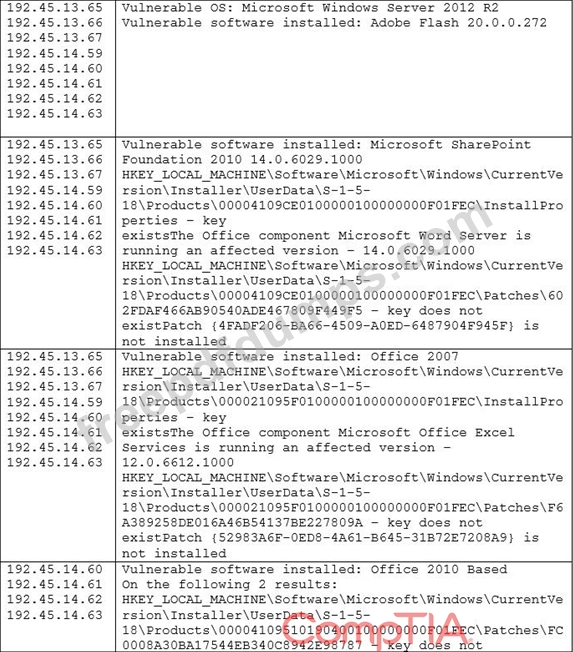
Which of the following would be the BEST way to remediate these findings and minimize similar findings in the future?

Which of the following would be the BEST way to remediate these findings and minimize similar findings in the future?
CS0-002 Exam Question 24
A vulnerability scan has returned the following information:
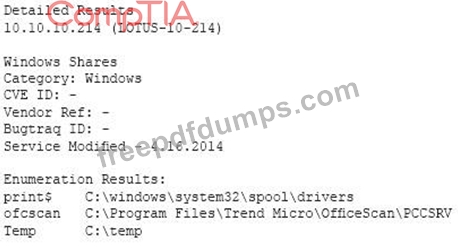
Which of the following describes the meaning of these results?

Which of the following describes the meaning of these results?
CS0-002 Exam Question 25
A company's incident response team is handling a threat that was identified on the network.
Security analysts have determined a web server is making multiple connections from TCP port
445 outbound to servers inside its subnet as well as at remote sites. Which of the following is the MOST appropriate next step in the incident response plan?
Security analysts have determined a web server is making multiple connections from TCP port
445 outbound to servers inside its subnet as well as at remote sites. Which of the following is the MOST appropriate next step in the incident response plan?

