CS0-002 Exam Question 26
A security analyst, who is working for a company that utilizes Linux servers, receives the following results from a vulnerability scan:
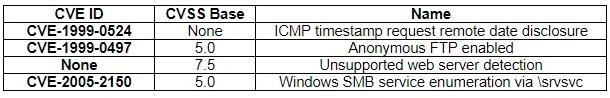
Which of the following is MOST likely a false positive?

Which of the following is MOST likely a false positive?
CS0-002 Exam Question 27
An investigation showed a worm was introduced from an engineer's laptop. It was determined the company does not provide engineers with company-owned laptops, which would be subject to company policy and technical controls.
Which of the following would be the MOST secure control implement?
Which of the following would be the MOST secure control implement?
CS0-002 Exam Question 28
The director of software development is concerned with recent web application security incidents, including the successful breach of a back-end database server. The director would like to work with the security team to implement a standardized way to design, build, and test web applications and the services that support them. Which of the following meets the criteria?
CS0-002 Exam Question 29
A developer wrote a script to make names and other PII data unidentifiable before loading a database export into the testing system. Which of the following describes the type of control that is being used?
CS0-002 Exam Question 30
An organization is moving its infrastructure to the cloud in an effort to meet the budget and reduce staffing requirements. The organization has three environments: development, testing, and production. These environments have interdependencies but must remain relatively segmented.
Which of the following methods would BEST secure the company's infrastructure and be the simplest to manage and maintain?
Which of the following methods would BEST secure the company's infrastructure and be the simplest to manage and maintain?

