CS0-002 Exam Question 261
An analyst is participating in the solution analysis process for a cloud-hosted SIEM platform to centralize log monitoring and alerting capabilities in the SOC.
Which of the following is the BEST approach for supply chain assessment when selecting a vendor?
Which of the following is the BEST approach for supply chain assessment when selecting a vendor?
CS0-002 Exam Question 262
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output:
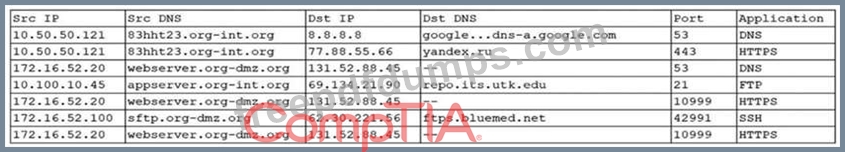
Which of the following should be the focus of the investigation?

Which of the following should be the focus of the investigation?
CS0-002 Exam Question 263
A company's data is still being exfiltered to business competitors after the implementation of a DLP solution. Which of the following is the most likely reason why the data is still being compromised?
CS0-002 Exam Question 264
A developer wrote a script to make names and other Pll data unidentifiable before loading a database export into the testing system Which of the following describes the type of control that is being used?
CS0-002 Exam Question 265
A vulnerability scan returned the following results for a web server that hosts multiple wiki sites:
Apache-HTTPD-cve-2014-023: Apache HTTPD: mod_cgid denial of service CVE-2014- Due to a flaw found in mog_cgid, a server using mod_cgid to host CGI scripts could be vulnerable to a DoS attack caused by a remote attacker who is exploiting a weakness in non-standard input, causing processes to hang indefinitely.
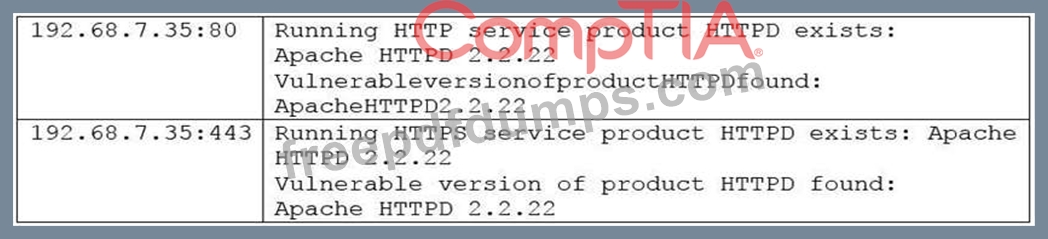
The security analyst has confirmed the server hosts standard CGI scripts for the wiki sites, does not have mod_cgid installed, is running Apache 2.2.22, and is not behind a WAF. The server is located in the DMZ, and the purpose of the server is to allow customers to add entries into a publicly accessible database.
Which of the following would be the MOST efficient way to address this finding?
Apache-HTTPD-cve-2014-023: Apache HTTPD: mod_cgid denial of service CVE-2014- Due to a flaw found in mog_cgid, a server using mod_cgid to host CGI scripts could be vulnerable to a DoS attack caused by a remote attacker who is exploiting a weakness in non-standard input, causing processes to hang indefinitely.

The security analyst has confirmed the server hosts standard CGI scripts for the wiki sites, does not have mod_cgid installed, is running Apache 2.2.22, and is not behind a WAF. The server is located in the DMZ, and the purpose of the server is to allow customers to add entries into a publicly accessible database.
Which of the following would be the MOST efficient way to address this finding?

