CS0-002 Exam Question 236
An analyst needs to provide a recommendation that will allow a custom-developed application to have full access to the system's processors and peripherals but still be contained securely from other applications that will be developed. Which of the following is the BEST technology for the analyst to recommend?
CS0-002 Exam Question 237
A cybersecurity consultant found common vulnerabilities across the following services used by multiple servers at an organization: VPN, SSH, and HTTPS. Which of the following is the MOST likely reason for the discovered vulnerabilities?
CS0-002 Exam Question 238
Which of the following sets of attributes BEST illustrates the characteristics of an insider threat from a security perspective?
CS0-002 Exam Question 239
An organization recently discovered that spreadsheet files containing sensitive financial data were improperly stored on a web server. The management team wants to find out if any of these files were downloaded by pubic users accessing the server. The results should be written to a text file and should induce the date. time, and IP address associated with any spreadsheet downloads. The web server's log file Is named webserver log, and the report We name should be accessreport.txt. Following is a sample of the web servefs.log file:
2017-0-12 21:01:12 GET /index.htlm - @4..102.33.7 - return=200 1622
Which of the following commands should be run if an analyst only wants to include entries in which spreadsheet was successfully downloaded?
2017-0-12 21:01:12 GET /index.htlm - @4..102.33.7 - return=200 1622
Which of the following commands should be run if an analyst only wants to include entries in which spreadsheet was successfully downloaded?
CS0-002 Exam Question 240
A security analyst is reviewing packet captures for a specific server that is suspected of containing malware and discovers the following packets:
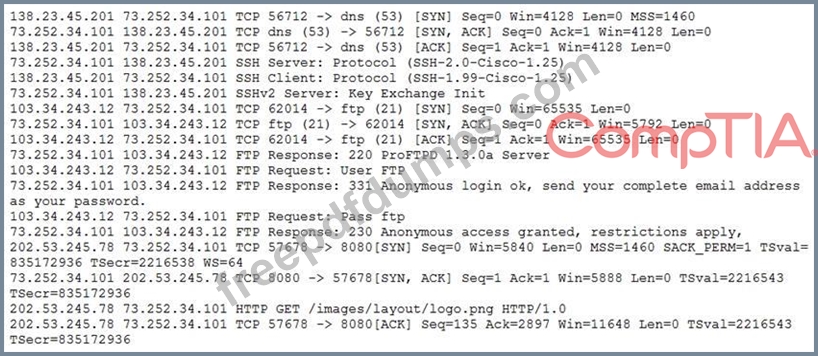
Which of the following traffic patterns or data would be MOST concerning to the security analyst?

Which of the following traffic patterns or data would be MOST concerning to the security analyst?

