CS0-002 Exam Question 246
Clients are unable to access a company's API to obtain pricing data.
An analyst discovers sources other than
clients are scraping the API for data, which is causing the servers to exceed available resources. Which of the following would be BEST to protect the availability of the APIs?
An analyst discovers sources other than
clients are scraping the API for data, which is causing the servers to exceed available resources. Which of the following would be BEST to protect the availability of the APIs?
CS0-002 Exam Question 247
An information security analyst on a threat-hunting team Is working with administrators to create a hypothesis related to an internally developed web application The working hypothesis is as follows:
* Due to the nature of the industry, the application hosts sensitive data associated with many clients and Is a significant target.
* The platform Is most likely vulnerable to poor patching and Inadequate server hardening, which expose vulnerable services.
* The application is likely to be targeted with SQL injection attacks due to the large number of reporting capabilities within the application.
As a result, the systems administrator upgrades outdated service applications and validates the endpoint configuration against an industry benchmark. The analyst suggests developers receive additional training on implementing identity and access management, and also implements a WAF to protect against SQL injection attacks Which of the following BEST represents the technique in use?
* Due to the nature of the industry, the application hosts sensitive data associated with many clients and Is a significant target.
* The platform Is most likely vulnerable to poor patching and Inadequate server hardening, which expose vulnerable services.
* The application is likely to be targeted with SQL injection attacks due to the large number of reporting capabilities within the application.
As a result, the systems administrator upgrades outdated service applications and validates the endpoint configuration against an industry benchmark. The analyst suggests developers receive additional training on implementing identity and access management, and also implements a WAF to protect against SQL injection attacks Which of the following BEST represents the technique in use?
CS0-002 Exam Question 248
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues The steering committee wants to rank the risks based on past incidents to improve the security program for next year Below is the incident register for the organization.
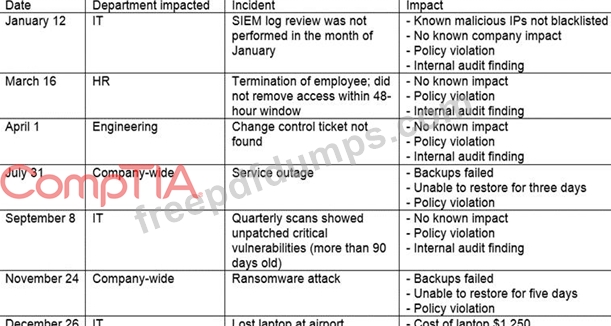
Which of the following should the organization consider investing in FIRST due to the potential impact of availability?

Which of the following should the organization consider investing in FIRST due to the potential impact of availability?
CS0-002 Exam Question 249
A team of security analysis has been alerted to potential malware activity. The initial examination indicates one of the affected workstations on beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team's NEXT step during the detection phase of this response process?
CS0-002 Exam Question 250
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output:
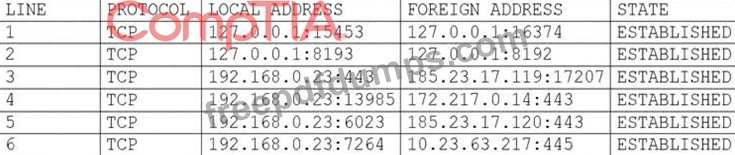
Which of the following lines indicates the computer may be compromised?

Which of the following lines indicates the computer may be compromised?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by Actual4test.com for Helping Passing CS0-002 Exam! Actual4test.com now offer the updated CS0-002 exam dumps, the Actual4test.com CS0-002 exam questions have been updated and answers have been corrected get the latest Actual4test.com CS0-002 pdf dumps with Exam Engine here:
(371 Q&As Dumps, 30%OFF Special Discount: Freepdfdumps)

