SC-300 Exam Question 1
You have a Microsoft 365 tenant.
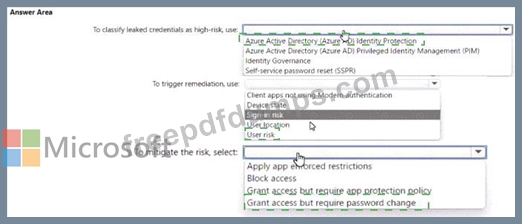
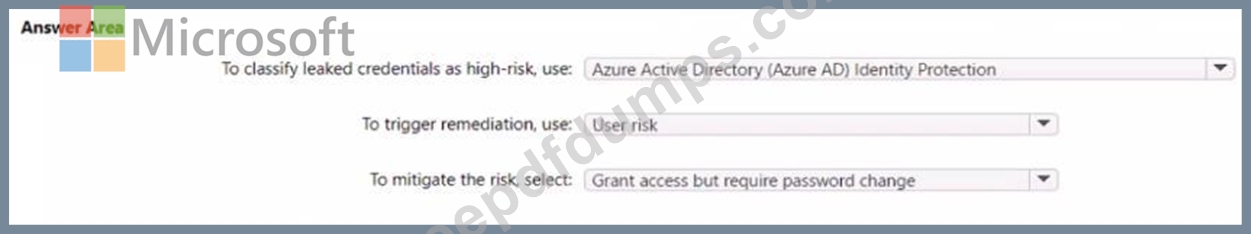
You need to Identity users who have leaked credentials. The solution must meet the following requirements:
* Identity sign-ms by users who are suspected of having leaked credentials.
* Flag the sign-ins as a high-risk event.
* Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options m the answer area.
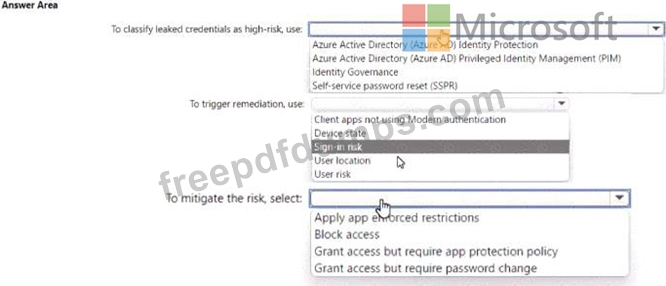
You need to Identity users who have leaked credentials. The solution must meet the following requirements:
* Identity sign-ms by users who are suspected of having leaked credentials.
* Flag the sign-ins as a high-risk event.
* Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options m the answer area.

SC-300 Exam Question 2
You have a Microsoft Exchange organization that uses an SMTP' address space of contoso.com.
Several users use their contoso.com email address for self-service sign up to Azure Active Directory (Azure AD).
You gain global administrator privileges to the Azure AD tenant that contains the self-signed users.
You need to prevent the users from creating user accounts in the contoso.com Azure AD tenant for self-service sign-up to Microsoft 365 services.
Which PowerShell cmdlet should you run?
Several users use their contoso.com email address for self-service sign up to Azure Active Directory (Azure AD).
You gain global administrator privileges to the Azure AD tenant that contains the self-signed users.
You need to prevent the users from creating user accounts in the contoso.com Azure AD tenant for self-service sign-up to Microsoft 365 services.
Which PowerShell cmdlet should you run?
SC-300 Exam Question 3
You have an Azure subscription that contains a user named User1. You need to meet the following requirements:
* Prevent User1 from being added as an owner of newly registered apps.
* Ensure that User1 can manage the application proxy settings.
* Ensure that User2 can register apps.
* Use the principle of least privilege.
Which role should you assign to User1?
* Prevent User1 from being added as an owner of newly registered apps.
* Ensure that User1 can manage the application proxy settings.
* Ensure that User2 can register apps.
* Use the principle of least privilege.
Which role should you assign to User1?
SC-300 Exam Question 4
You have a Microsoft 365 tenant.
The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain.
Users connect to the internet by using a hardware firewall at your company. The users authenticate to the firewall by using their Active Directory credentials.
You plan to manage access to external applications by using Azure AD.
You need to use the firewall logs to create a list of unmanaged external applications and the users who access them.
What should you use to gather the information?
The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain.
Users connect to the internet by using a hardware firewall at your company. The users authenticate to the firewall by using their Active Directory credentials.
You plan to manage access to external applications by using Azure AD.
You need to use the firewall logs to create a list of unmanaged external applications and the users who access them.
What should you use to gather the information?
SC-300 Exam Question 5
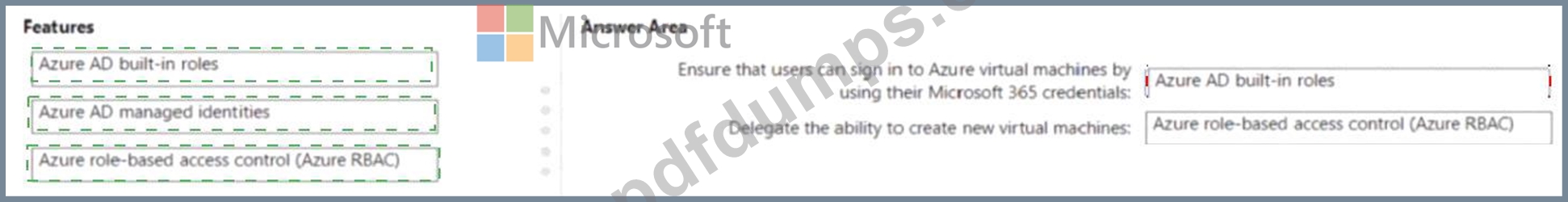
You have a Microsoft 365 E5 subscription and an Azure subscription. You need to meet the following requirements:
* Ensure that users can sign in to Azure virtual machines by using their Microsoft 365 credentials.
* Delegate the ability to create new virtual machines.
What should you use for each requirement? To answer, drag the appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
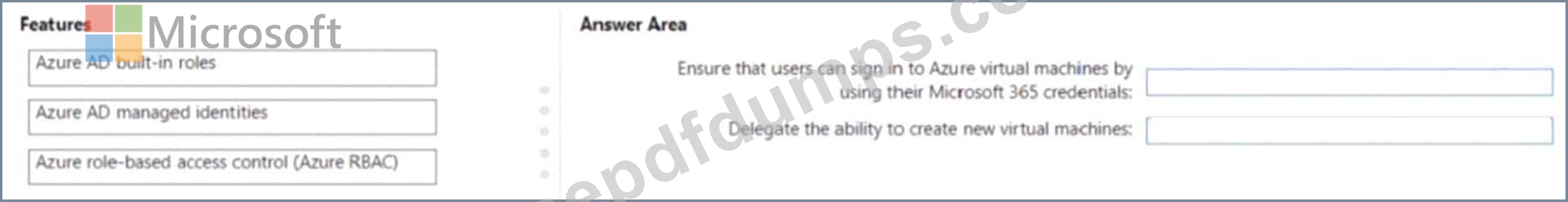
* Ensure that users can sign in to Azure virtual machines by using their Microsoft 365 credentials.
* Delegate the ability to create new virtual machines.
What should you use for each requirement? To answer, drag the appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.