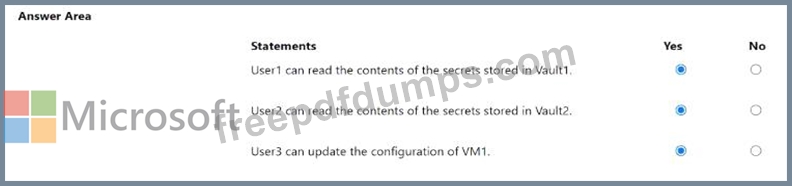
SC-300 Exam Question 41
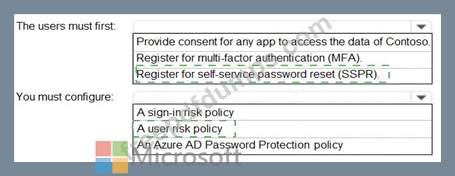
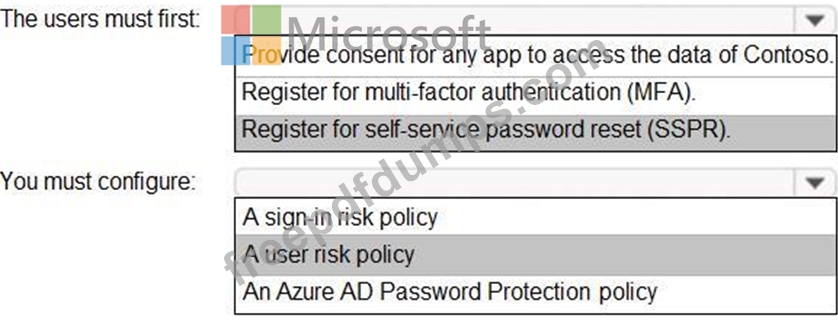
You need to meet the technical requirements for the probability that user identities were compromised.
What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 42
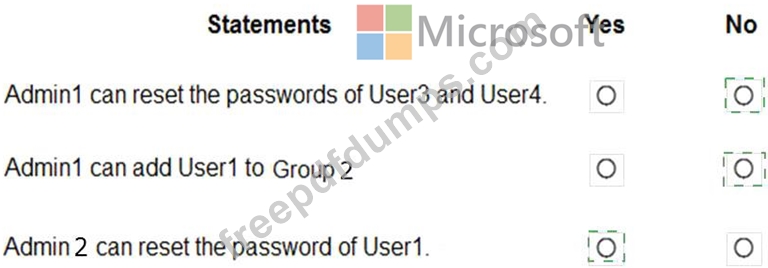
You have an Azure Active Directory (Azure AD) tenant that contains an administrative unit named Department1.
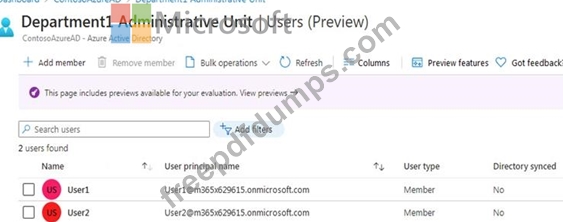
Department1 has the users shown in the Users exhibit. (Click the Users tab.)
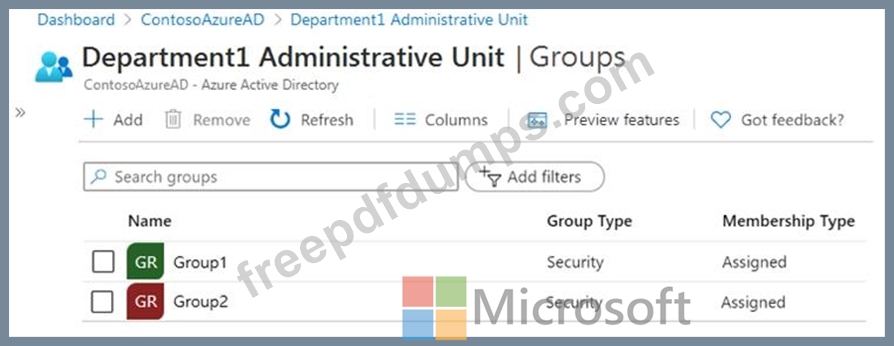
Department1 has the groups shown in the Groups exhibit. (Click the Groups tab.)
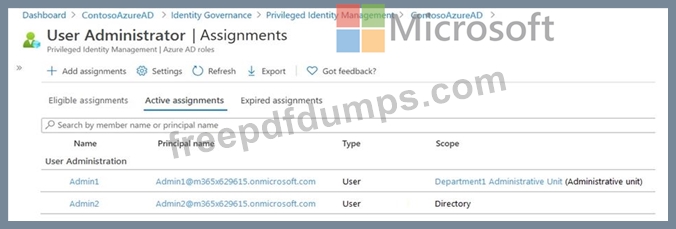
Department1 has the user administrator assignments shown in the Assignments exhibit. (Click the Assignments tab.)
The members of Group2 are shown in the Group2 exhibit. (Click the Group2 tab.)
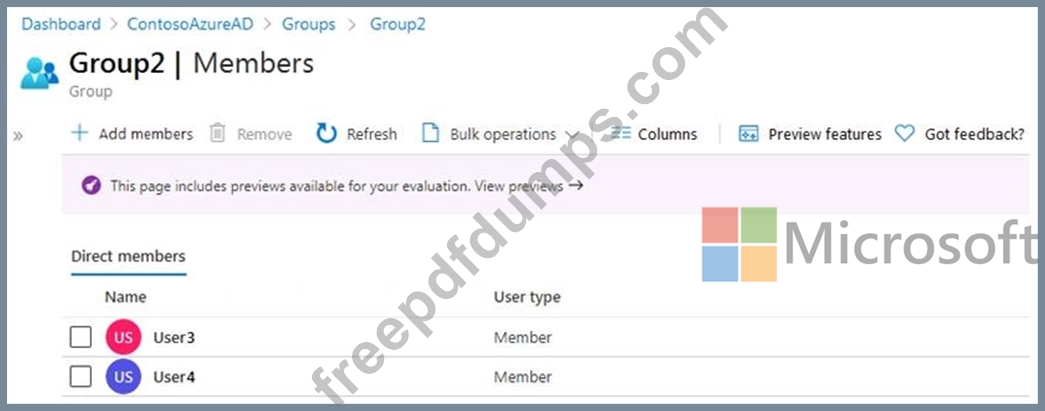
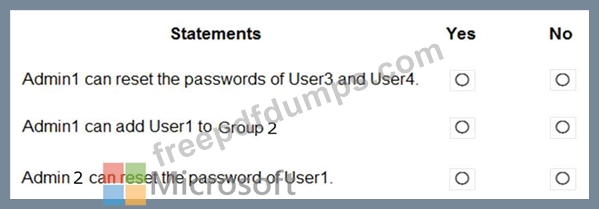
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
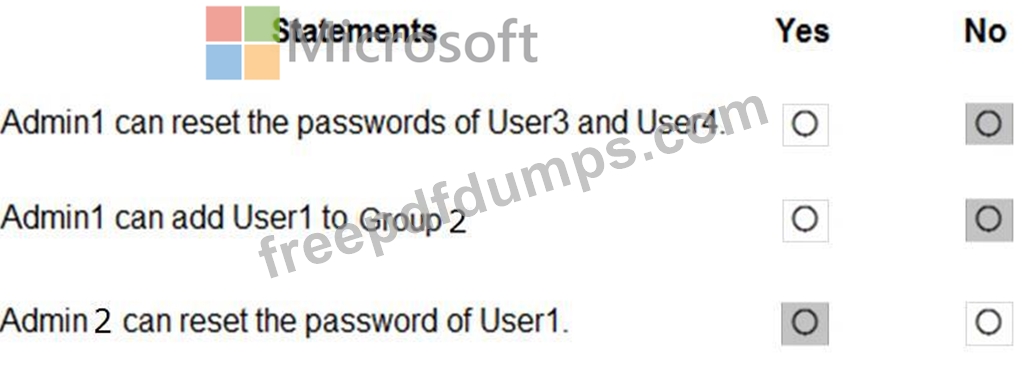
Department1 has the users shown in the Users exhibit. (Click the Users tab.)

Department1 has the groups shown in the Groups exhibit. (Click the Groups tab.)

Department1 has the user administrator assignments shown in the Assignments exhibit. (Click the Assignments tab.)

The members of Group2 are shown in the Group2 exhibit. (Click the Group2 tab.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 43
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the objects shown in the following table.
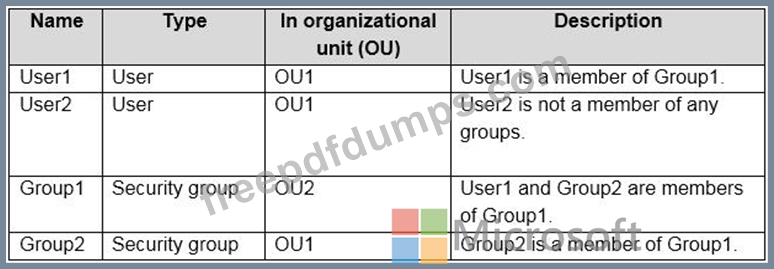
You install Azure AD Connect. You configure the Domain and OU filtering settings as shown in the Domain and OU Filtering exhibit. (Click the Domain and OU Filtering tab.)
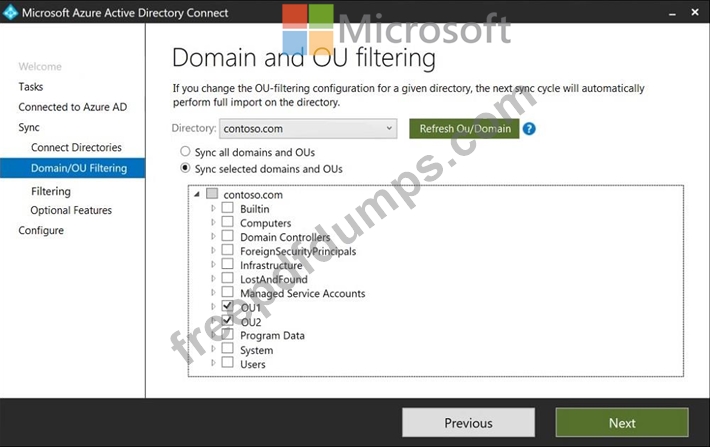
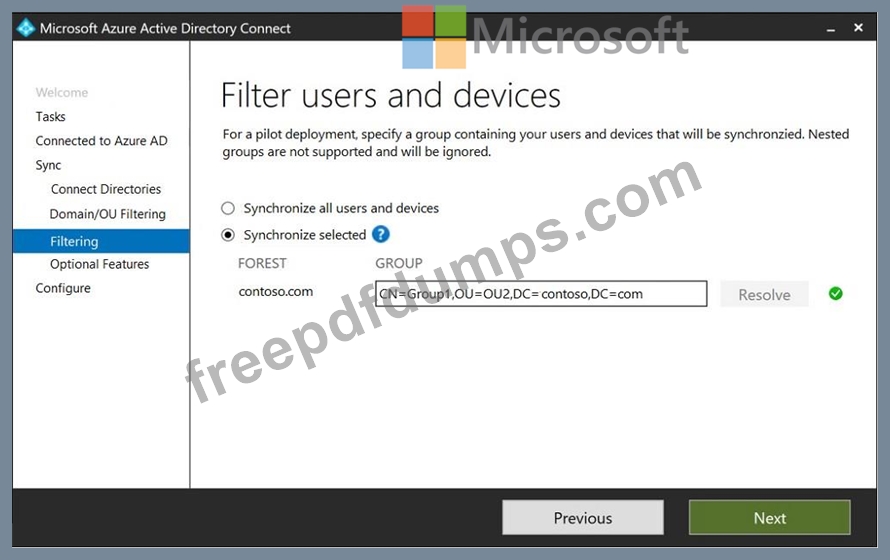
You configure the Filter users and devices settings as shown in the Filter Users and Devices exhibit. (Click the Filter Users and Devices tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.


You install Azure AD Connect. You configure the Domain and OU filtering settings as shown in the Domain and OU Filtering exhibit. (Click the Domain and OU Filtering tab.)

You configure the Filter users and devices settings as shown in the Filter Users and Devices exhibit. (Click the Filter Users and Devices tab.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.

SC-300 Exam Question 44
You create the Azure Active Directory (Azure AD) users shown in the following table.

On February 1, 2021, you configure the multi-factor authentication (MFA) settings as shown in the following exhibit.

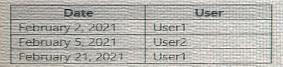
The users authentication to Azure AD on their devices as shown in the following table.
On February 26, 2021, what will the multi-factor auth status be for each user?

On February 1, 2021, you configure the multi-factor authentication (MFA) settings as shown in the following exhibit.

The users authentication to Azure AD on their devices as shown in the following table.

On February 26, 2021, what will the multi-factor auth status be for each user?
SC-300 Exam Question 45
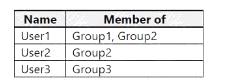
You have an Azure subscription named Sub1 that contains two resource groups named RG1 and RG2. Sub1 contains the users shown in the following table.
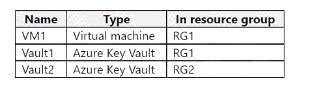
Sub1 contains the resources shown in the following table.
You create the role-based access control (RBAC) role assignments shown in the following table.
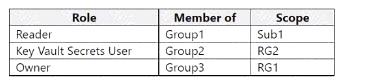
For each of the following statements, select Yes if the statement is true. Otherwise, select No NOTE: Each correct selection is worth one point.


Sub1 contains the resources shown in the following table.

You create the role-based access control (RBAC) role assignments shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No NOTE: Each correct selection is worth one point.