SC-300 Exam Question 51
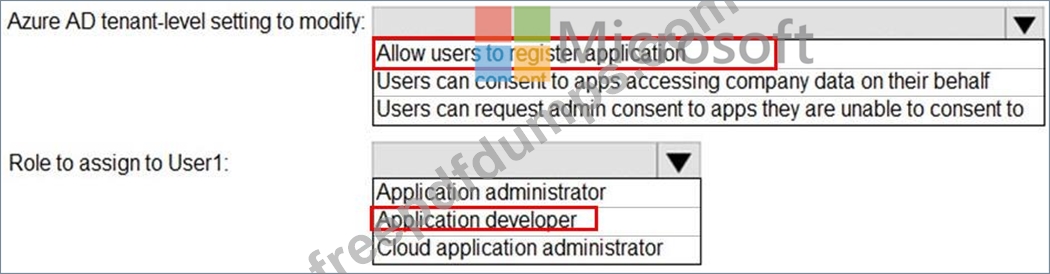
You need to configure app registration in Azure AD to meet the delegation requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
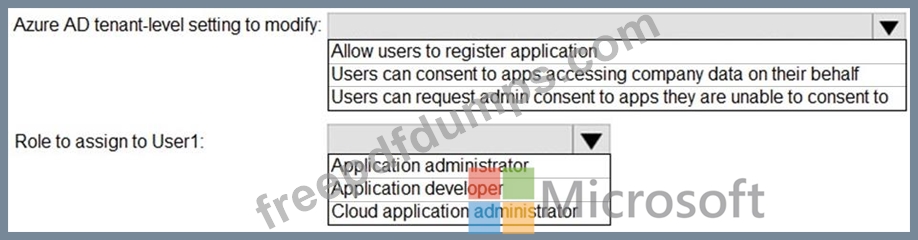
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 52
You have a Microsoft 365 tenant.
The Azure Active Directory (Azure AD) tenant contains the groups shown in the following table.
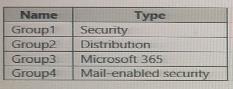
In Azure AD. you add a new enterprise application named Appl. Which groups can you assign to App1?
The Azure Active Directory (Azure AD) tenant contains the groups shown in the following table.

In Azure AD. you add a new enterprise application named Appl. Which groups can you assign to App1?
SC-300 Exam Question 53
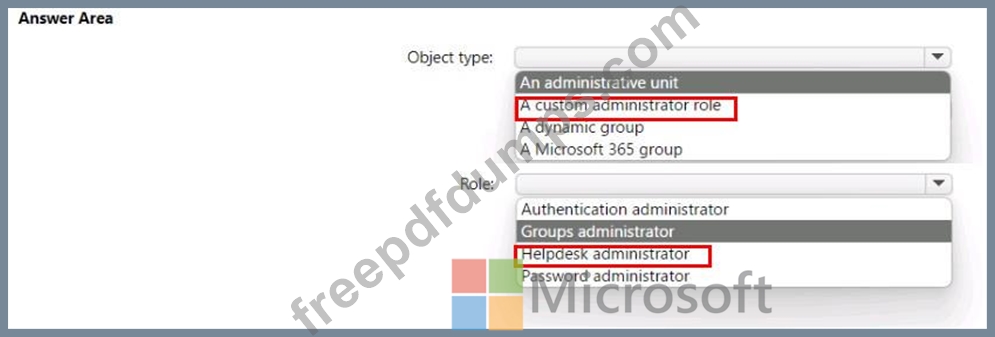
You have a Microsoft 365 tenant that has 5,000 users. One hundred of the users are executives. The executives have a dedicated support team.
You need to ensure that the support team can reset passwords and manage multi-factor authentication (MFA) settings for only the executives. The solution must use the principle of least privilege.
Which object type and Azure Active Directory (Azure AD) role should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
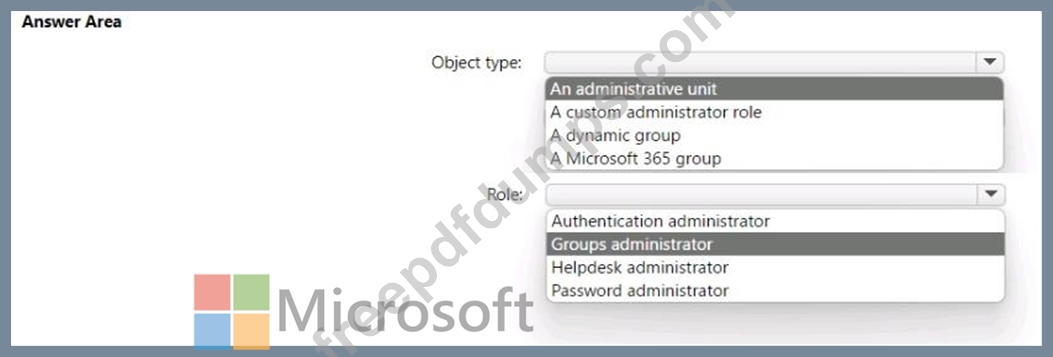
You need to ensure that the support team can reset passwords and manage multi-factor authentication (MFA) settings for only the executives. The solution must use the principle of least privilege.
Which object type and Azure Active Directory (Azure AD) role should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 54
You have a Microsoft 365 tenant.
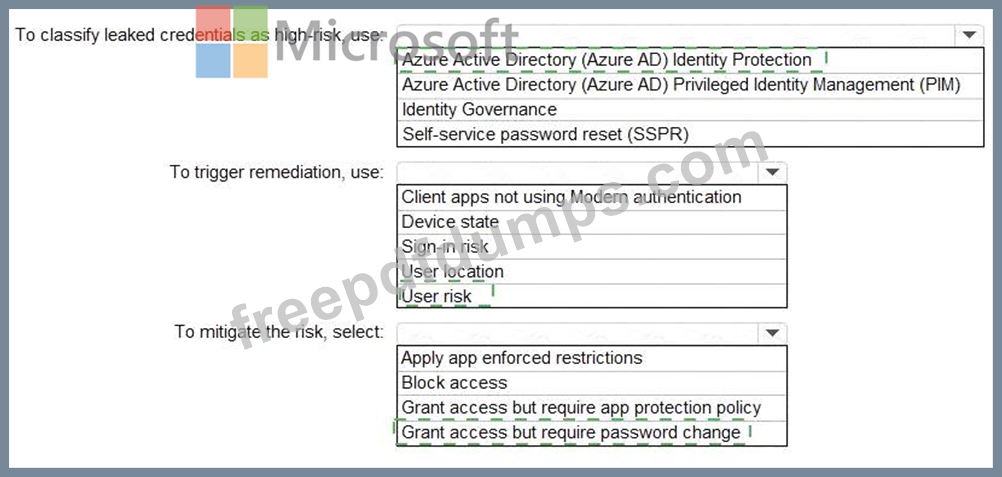
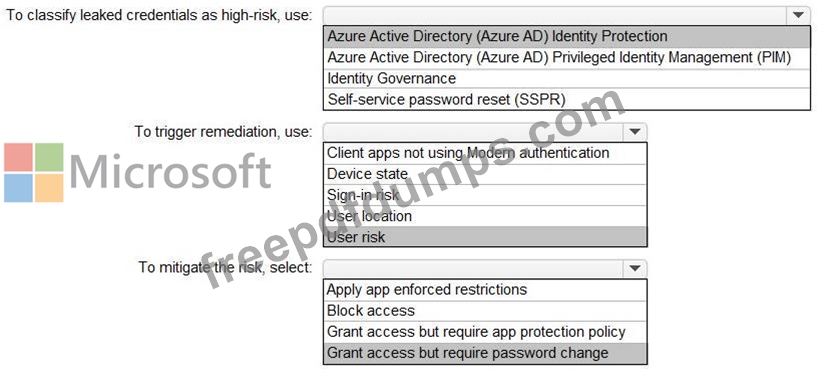
You need to identify users who have leaked credentials. The solution must meet the following requirements.
* Identity sign-Ins by users who ate suspected of having leaked credentials.
* Rag the sign-ins as a high risk event.
* Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
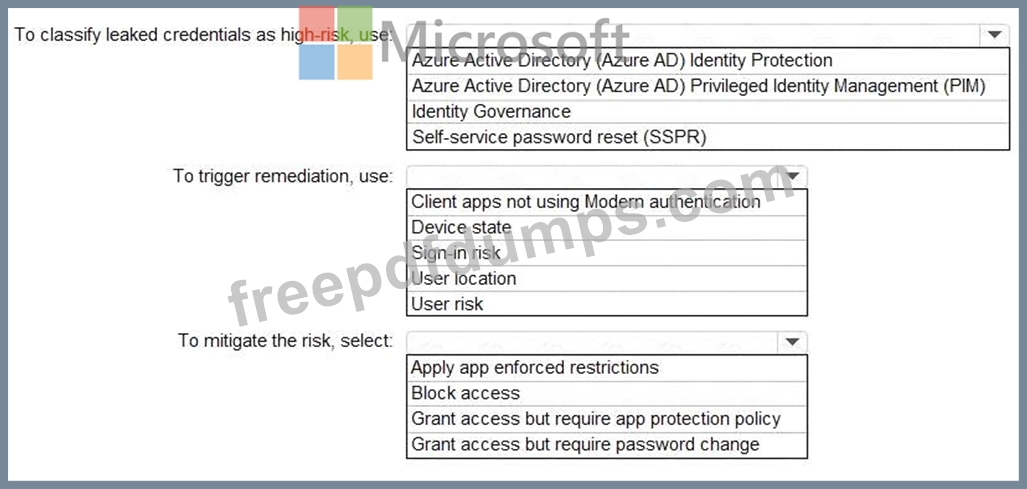
You need to identify users who have leaked credentials. The solution must meet the following requirements.
* Identity sign-Ins by users who ate suspected of having leaked credentials.
* Rag the sign-ins as a high risk event.
* Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 55
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant.
You have 100 IT administrators who are organized into 10 departments.
You create the access review shown in the exhibit. (Click the Exhibit tab.)
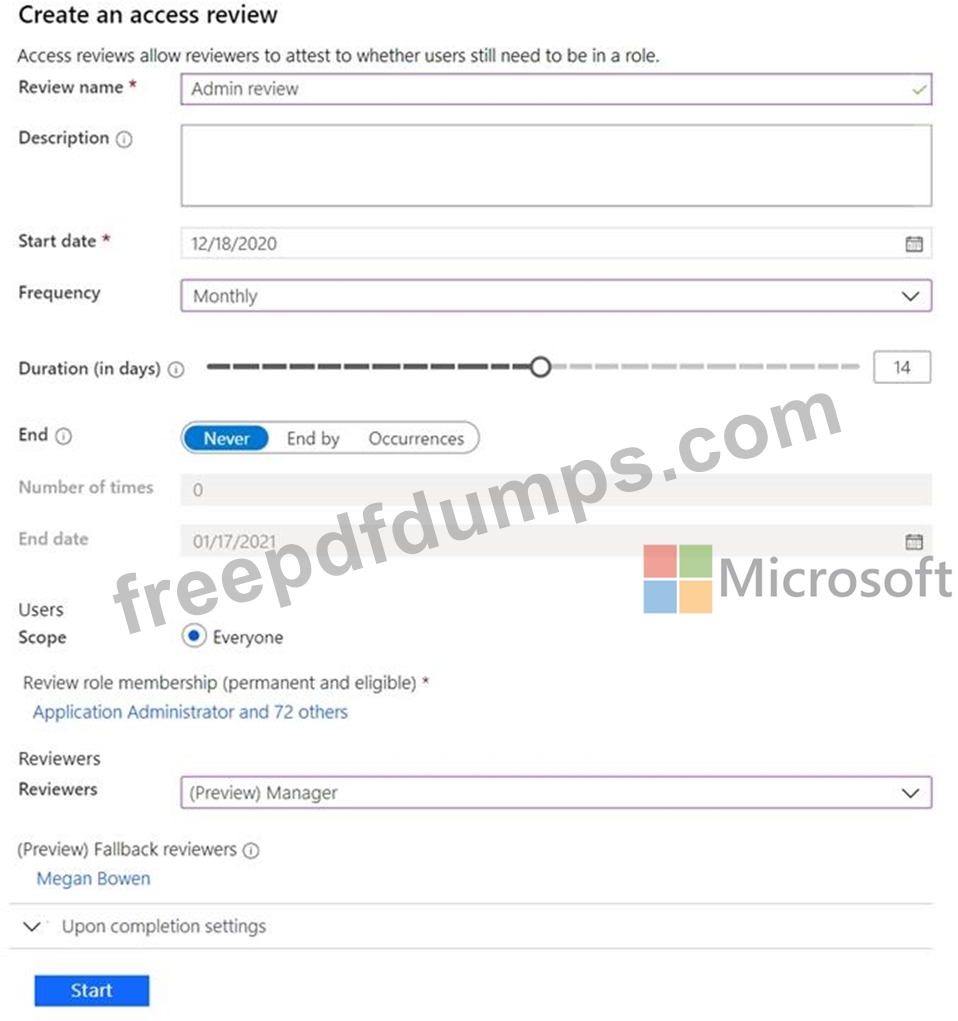
You discover that all access review requests are received by Megan Bowen.
You need to ensure that the manager of each department receives the access reviews of their respective department.
Solution: You modify the properties of the IT administrator user accounts.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant.
You have 100 IT administrators who are organized into 10 departments.
You create the access review shown in the exhibit. (Click the Exhibit tab.)

You discover that all access review requests are received by Megan Bowen.
You need to ensure that the manager of each department receives the access reviews of their respective department.
Solution: You modify the properties of the IT administrator user accounts.
Does this meet the goal?