SC-300 Exam Question 31
You have an Azure Active Directory (Azure AD) tenant that contains the objects shown in the following table.
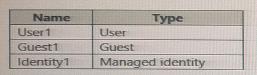
Which objects can you add as eligible in Azure Privileged identity Management (PIM) for an Azure AD role?

Which objects can you add as eligible in Azure Privileged identity Management (PIM) for an Azure AD role?
SC-300 Exam Question 32
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1. An administrator deletes User1. You need to identity the following:
* How many days after the account of User1 is deleted can you restore the account?
* Which is the least privileged role that can be used to restore User1?
What should you identify? To answer, select the appropriate options in the answer are a. NOTE: Each correct selection is worth one point.

* How many days after the account of User1 is deleted can you restore the account?
* Which is the least privileged role that can be used to restore User1?
What should you identify? To answer, select the appropriate options in the answer are a. NOTE: Each correct selection is worth one point.

SC-300 Exam Question 33
You have a Microsoft 365 tenant named contoso.com.
Guest user access is enabled.
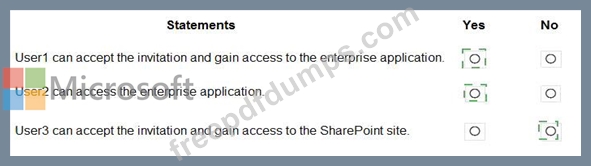
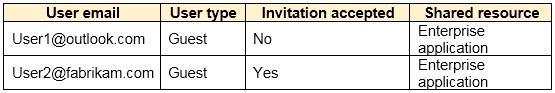
Users are invited to collaborate with contoso.com as shown in the following table.
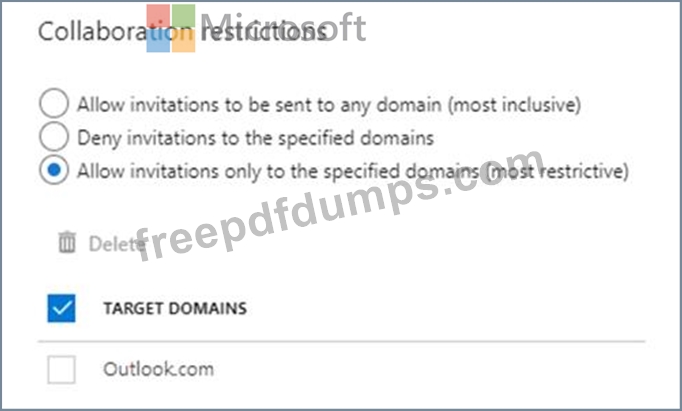
From the External collaboration settings in the Azure Active Directory admin center, you configure the Collaboration restrictions settings as shown in the following exhibit.
From a Microsoft SharePoint Online site, a user invites [email protected] to the site.
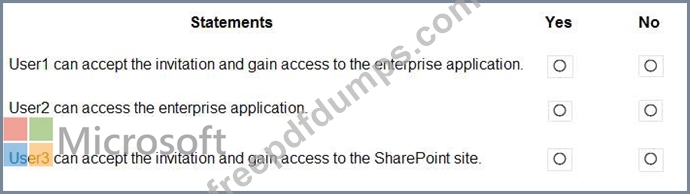
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Guest user access is enabled.
Users are invited to collaborate with contoso.com as shown in the following table.

From the External collaboration settings in the Azure Active Directory admin center, you configure the Collaboration restrictions settings as shown in the following exhibit.

From a Microsoft SharePoint Online site, a user invites [email protected] to the site.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 34
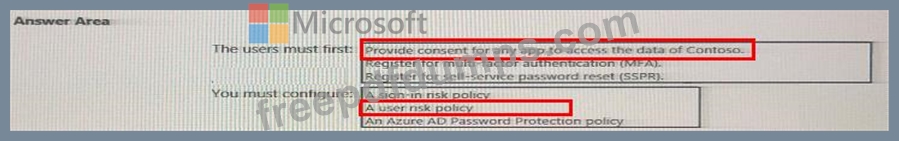
You need to meet the technical requirements for the probability that user identifies were compromised.
What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
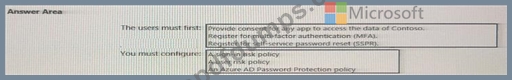
What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 35
You need to track application access assignments by using Identity Governance. The solution must meet the delegation requirements.
What should you do first?
What should you do first?