SC-400 Exam Question 6
Case Study 2 - Contoso, Ltd
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in Seattle, Boston, and Johannesburg.
Existing Environment
Microsoft 365 Environment
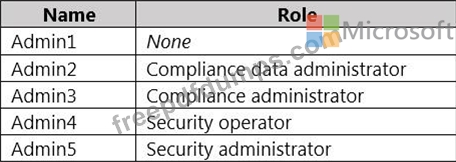
Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown in the following table.
Users store data in the following locations:
SharePoint sites
OneDrive accounts
Exchange email
Exchange public folders
Teams chats
Teams channel messages
When users in the research department create documents, they must add a 10-digit project code to each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
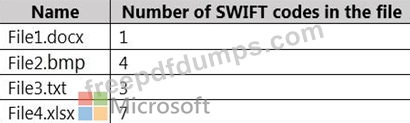
Site2 contains the files shown in the following table.
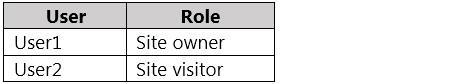
Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.
Site3 stores documents related to the company's projects. The documents are organized in a folder hierarchy based on the project.
Site4 has the following two retention policies applied:
Name: Site4RetentionPolicy1
- Locations to apply the policy: Site4
- Delete items older than: 2 years
- Delete content based on: When items were created
Name: Site4RetentionPolicy2
- Locations to apply the policy: Site4
- Retain items for a specific period: 4 years
- Start the retention period based on: When items were created
- At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research department documents were leaked.
Requirements
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
Name: DLPpolicy1
Locations to apply the policy: Site2
Conditions:
- Content contains any of these sensitive info types: SWIFT Code
- Instance count: 2 to any
Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
All administrative users must be able to review DLP reports.
Whenever possible, the principle of least privilege must be used.
For all users, all Microsoft 365 data must be retained for at least one year.
Confidential documents must be detected and protected by using Microsoft 365.
Site1 documents that include credit card numbers must be labeled automatically.
All administrative users must be able to create Microsoft 365 sensitivity labels.
After a project is complete, the documents in Site3 that relate to the project must be retained for
10 years.
You need to meet the technical requirements for the Site3 documents.
What should you create?
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in Seattle, Boston, and Johannesburg.
Existing Environment
Microsoft 365 Environment
Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown in the following table.

Users store data in the following locations:
SharePoint sites
OneDrive accounts
Exchange email
Exchange public folders
Teams chats
Teams channel messages
When users in the research department create documents, they must add a 10-digit project code to each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
Site2 contains the files shown in the following table.

Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.

Site3 stores documents related to the company's projects. The documents are organized in a folder hierarchy based on the project.
Site4 has the following two retention policies applied:
Name: Site4RetentionPolicy1
- Locations to apply the policy: Site4
- Delete items older than: 2 years
- Delete content based on: When items were created
Name: Site4RetentionPolicy2
- Locations to apply the policy: Site4
- Retain items for a specific period: 4 years
- Start the retention period based on: When items were created
- At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research department documents were leaked.
Requirements
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
Name: DLPpolicy1
Locations to apply the policy: Site2
Conditions:
- Content contains any of these sensitive info types: SWIFT Code
- Instance count: 2 to any
Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
All administrative users must be able to review DLP reports.
Whenever possible, the principle of least privilege must be used.
For all users, all Microsoft 365 data must be retained for at least one year.
Confidential documents must be detected and protected by using Microsoft 365.
Site1 documents that include credit card numbers must be labeled automatically.
All administrative users must be able to create Microsoft 365 sensitivity labels.
After a project is complete, the documents in Site3 that relate to the project must be retained for
10 years.
You need to meet the technical requirements for the Site3 documents.
What should you create?
SC-400 Exam Question 7
Hotspot Question
At the end of a project you upload project documents to a Microsoft SharePoint Online library that contains many fifes. Files that have the following naming format must be labeled as Project Documents:
- aei_AA989.docx
- bci_WS098.docx
- cei_DF112.docx
- ebc_QQ454.docx
- ecc_BB565.docx
You plan to create an auto-apply retention label policy.
What should you use to identify the files, and which regular expression should you use? To answer, select the appropriate options in the answer area.

At the end of a project you upload project documents to a Microsoft SharePoint Online library that contains many fifes. Files that have the following naming format must be labeled as Project Documents:
- aei_AA989.docx
- bci_WS098.docx
- cei_DF112.docx
- ebc_QQ454.docx
- ecc_BB565.docx
You plan to create an auto-apply retention label policy.
What should you use to identify the files, and which regular expression should you use? To answer, select the appropriate options in the answer area.

SC-400 Exam Question 8
You need to protect documents that contain credit card numbers from being opened by users outside your company. The solution must ensure that users at your company can open the documents.
What should you use?
What should you use?
SC-400 Exam Question 9
Hotspot Question
You have a Microsoft 365 E5 subscription that contains the users and groups shown in the following table.

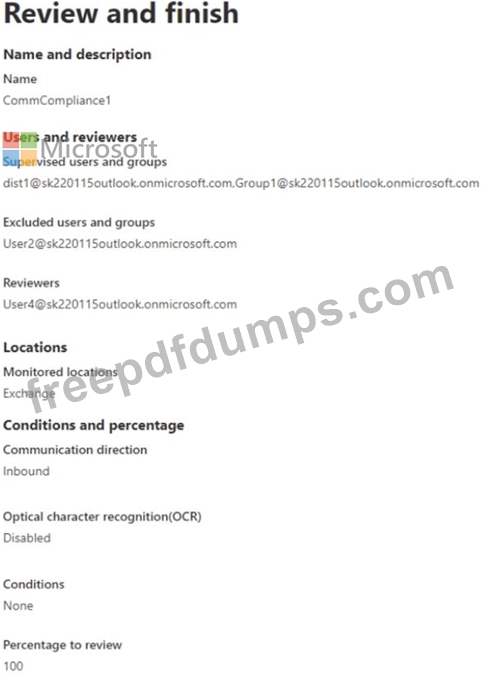
You create the communication compliance policy as shown in the exhibit. (Click the Exhibit tab.)
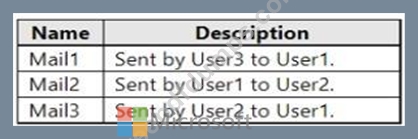
Four emails are sent as shown in the following table.
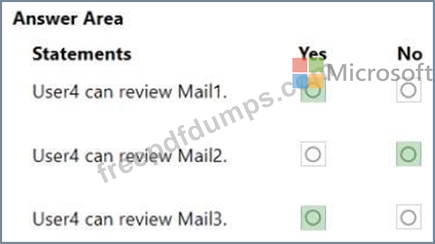
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that contains the users and groups shown in the following table.

You create the communication compliance policy as shown in the exhibit. (Click the Exhibit tab.)

Four emails are sent as shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

SC-400 Exam Question 10
You have a data loss prevention (DLP) policy configured for endpoints as shown in the following exhibit.
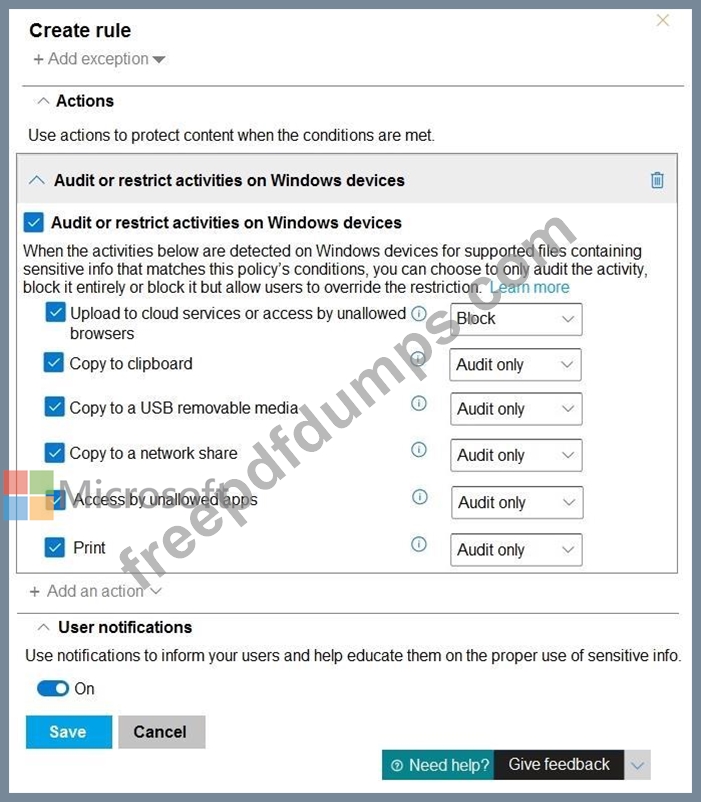
From a computer named Computer1, a user can sometimes upload files to cloud services and sometimes cannot. Other users experience the same issue.
What are two possible causes of the issue? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.

From a computer named Computer1, a user can sometimes upload files to cloud services and sometimes cannot. Other users experience the same issue.
What are two possible causes of the issue? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.