CS0-002 Exam Question 106
A network appliance manufacturer is building a new generation of devices and would like to include chipset security improvements. The management team wants the security team to implement a method to prevent security weaknesses that could be reintroduced by downgrading the firmware version on the chipset. Which of the following would meet this objective?
CS0-002 Exam Question 107
While investigating reports or issues with a web server, a security analyst attempts to log in remotely and recedes the following message:
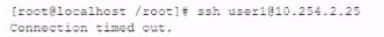
The analyst accesses the server console, and the following console messages are displayed:

The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:
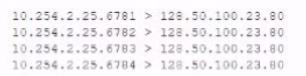
Which of the following is the BEST step for the analyst to lake next in this situation?
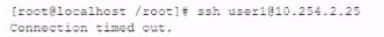
The analyst accesses the server console, and the following console messages are displayed:

The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:

Which of the following is the BEST step for the analyst to lake next in this situation?
CS0-002 Exam Question 108
An organisation is assessing risks so it can prioritize its mitigation actions. Following are the risks and their probability and impact:
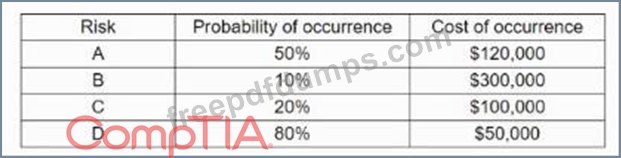
Which of the following is the order of priority for risk mitigation from highest to lowest?

Which of the following is the order of priority for risk mitigation from highest to lowest?
CS0-002 Exam Question 109
A company has decided to process credit card transactions directly. Which of the following would meet the requirements for scanning this type of data?
CS0-002 Exam Question 110
During routine monitoring a security analyst identified the following enterpnse network traffic:
Packet capture output:
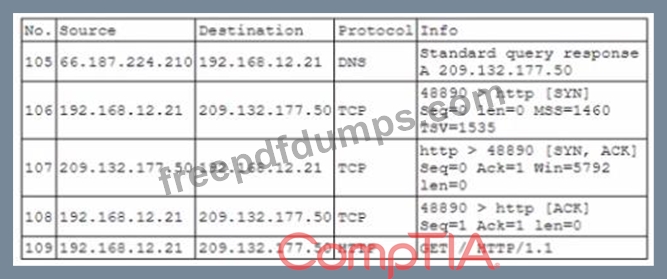
Which of the following BEST describes what the security analyst observed?
Packet capture output:

Which of the following BEST describes what the security analyst observed?

